The guest user accounts are special in Fortigate and unlike regular local Firewall user accounts. The flow of creating them is:
Let's configure it.
First, you create Groups, which serve, in this case, as a template for various parameters users can/must have later:
User & Device -> User Groups -> New .. -> Type: Guest
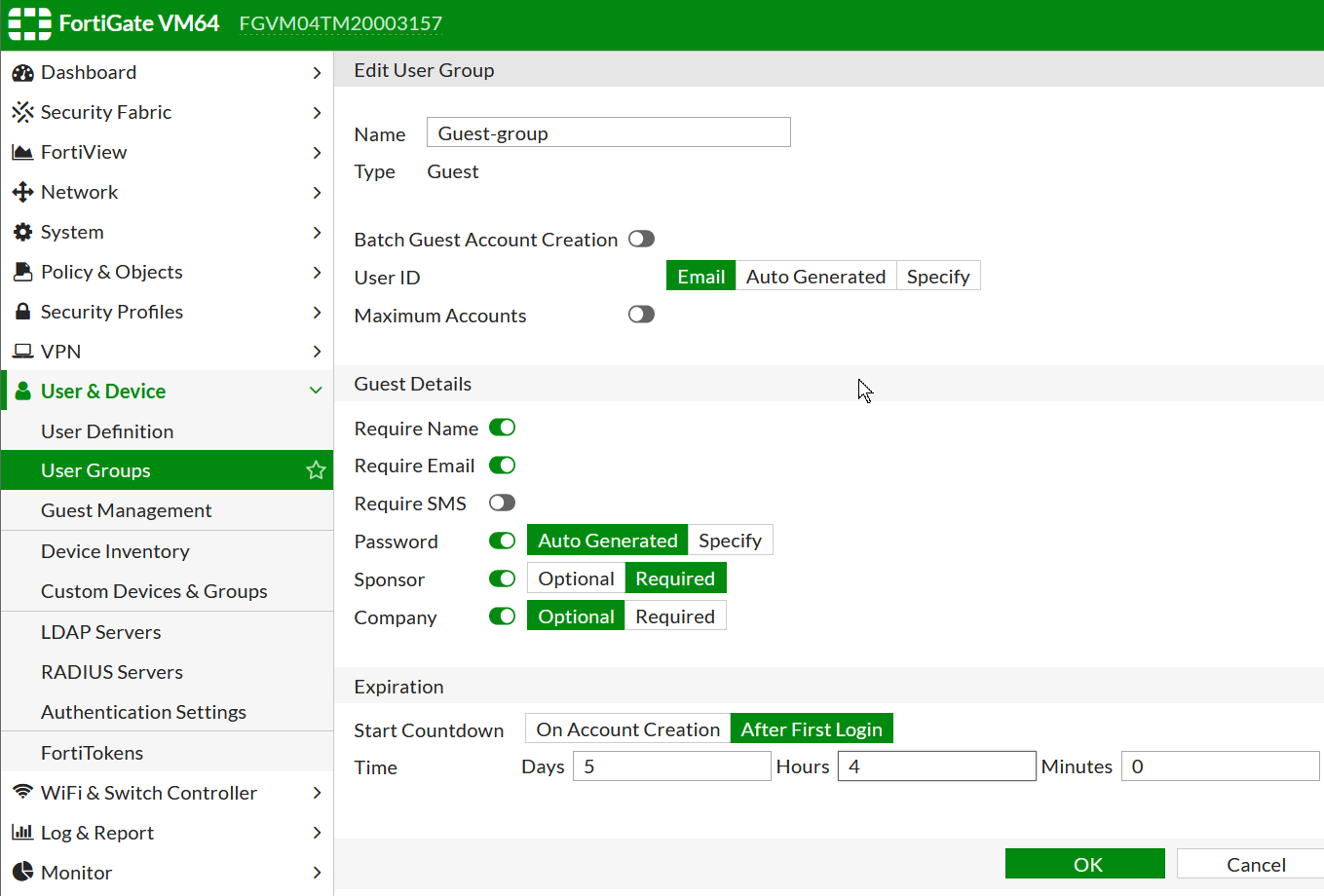
If you enable "Batch Guest Account Creation" then all the configs become grayed out and all the details of the to-be created users will auto-randomly generated.
(Optional) Create Guest users admin to manage them and assign relevant Groups
Such admin can only see the page of managing these Guest users and that is it.
System -> Administrators -> New .. -> Type: Restrict admin to guest account provisioning only:
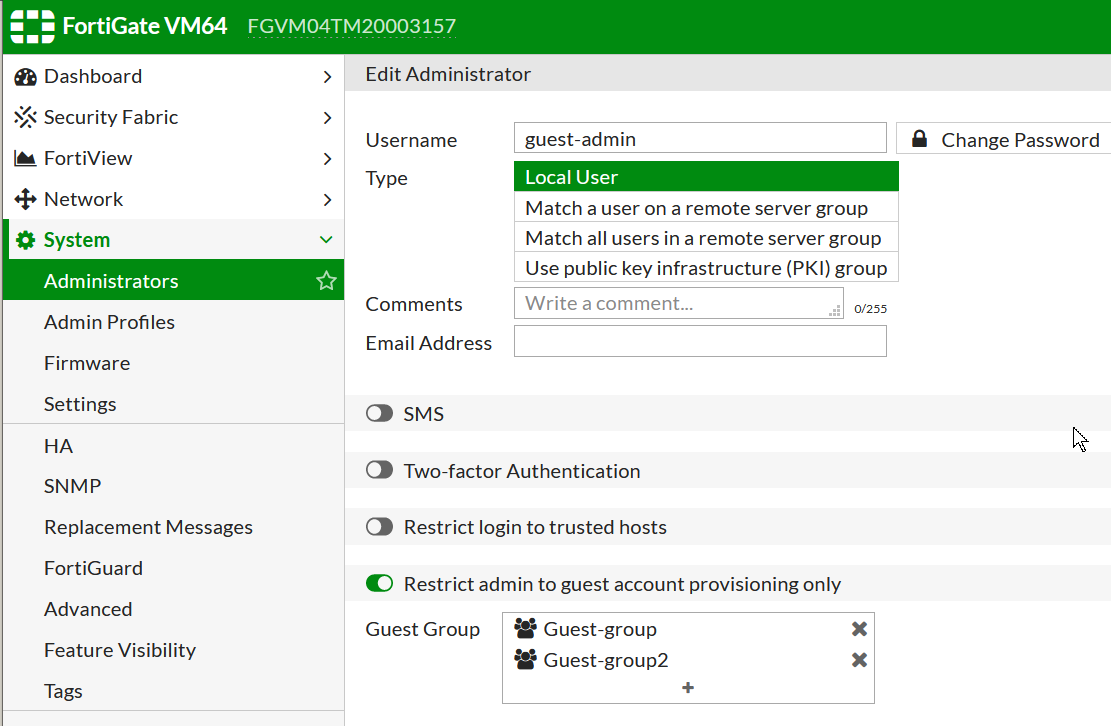
This admin has to have access to the Management IP as a usual admin:
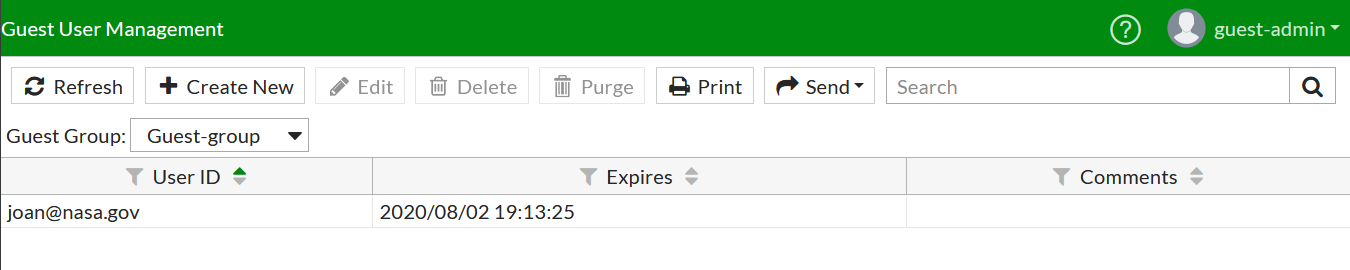
Create Guest users
User & Device -> Guest Management -> New ..
Pay attention to the right upper corner to pick the correct group for the new to-be created user.
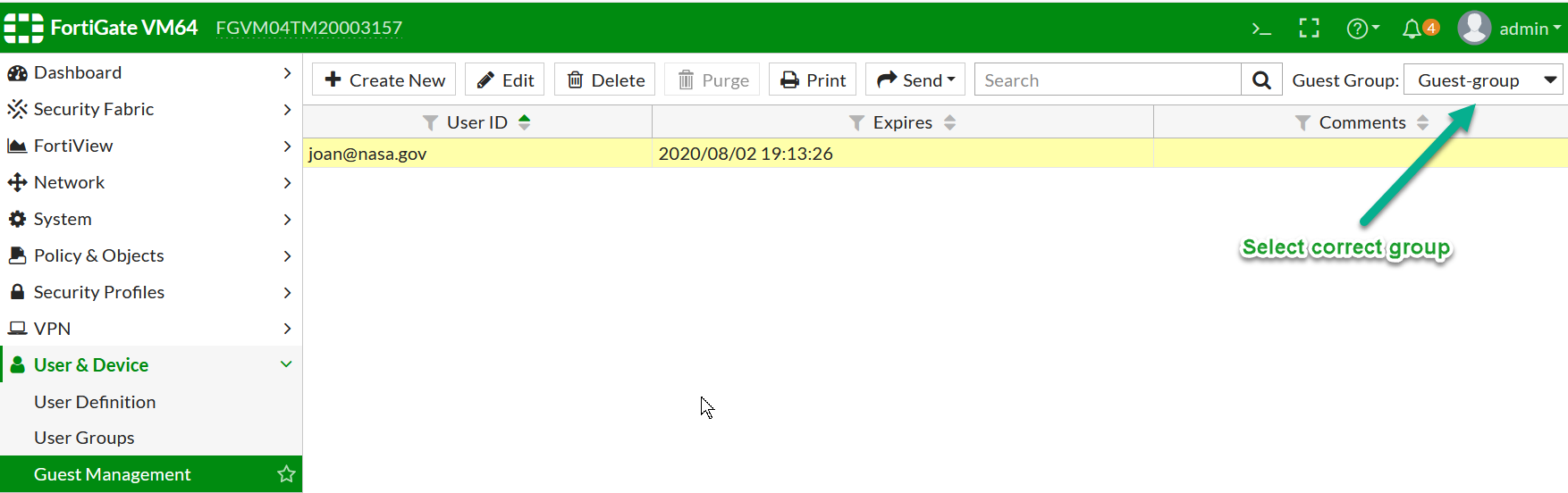
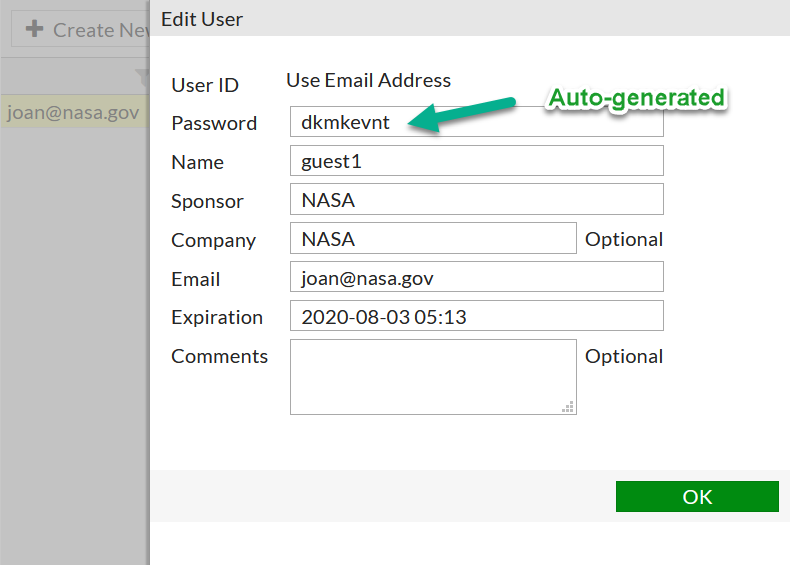
Use the created Groups
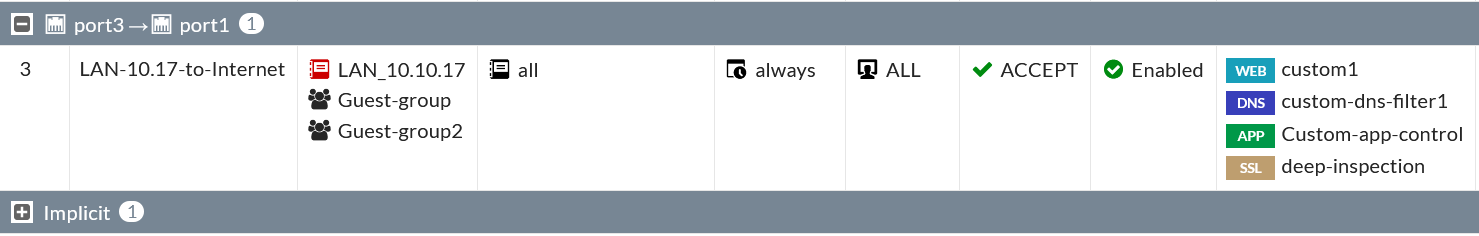
Finally, we can use the Guest groups in Security rules or WiFi SSID for the Captive Portal for authenticaton.
Here is the example of Security rule. A user will have to first browse somewhere to get the login page.
Full CLI configuration:
config user group edit "SSO_Guest_Users" next edit "Guest-group" set group-type guest set user-name enable set sponsor mandatory set expire-type first-successful-login set expire 446400 config guest edit "joan@nasa.gov" set name "guest1" set password ENC y3UDU+HYxl2n7KBFwPXNkd1BD2XmoAKyga50LtyL+qk+GLcwPDGHyw8hzkY9Wl0Q7wYYm4dOWuqMoDAzvQ1MsxyoxJsLag+esNBC4nGONVC+tRqyWSjA+8xvyiZykgwB3Urj0ylv6vd99mVk0XiwHtd2S/GLB7/1DsfQtinp6NwH4FF3g+3YPni7fThHwWQjnMfH3w== set sponsor "NASA" set company "NASA" set email "joan@nasa.gov" set expiration 2020-08-03 05:13:27 next end next edit "Guest-group2" set group-type guest set user-name enable set expire-type first-successful-login set expire 878400 config guest edit "johnny@nsa.gov" set name "guest2" set password ENC 41+u3YABUwTLctu56UTIni2P7rRnr3edfCKOfH/RJatGi7znh8kpcxc03vJTciH4J7/CDmBVESD4foPi5hMV+u9DQLzQ2AN2sxKMcB+9fJ/O2RhlVRoBwR7SN/is2G2Tra3pMA1lkWzJhMAcXfQnB55YcYq5UnXqGYDNhNt+I8+1CDyowlxIxWpS5grwPIYJEiWQCQ== set sponsor "NSA" set company "NSA" set email "johnny@nsa.gov" set expiration 878400 next end nextendOptional guest users admin:
config system admin edit "guest-admin" set vdom "root" set guest-auth enable set guest-usergroups "Guest-group" "Guest-group2" set password ENC SH2SUStSlY72bDN/7nYPYJGaKNHPdtjsd4BLiYwKzXu+N/B19BHiX899iakQ6k= nextendLAN to Internet wired networks rule:
edit 3 set name "LAN-10.17-to-Internet" set uuid cdfe8fee-ca85-51ea-5c07-b2311d5406cd set srcintf "port3" set dstintf "port1" set srcaddr "LAN_10.10.17" set dstaddr "all" set action accept set schedule "always" set service "ALL" set utm-status enable set fsso disable set groups "Guest-group" "Guest-group2" <-- Guest user groups set webfilter-profile "custom1" set dnsfilter-profile "custom-dns-filter1" set application-list "Custom-app-control" set ssl-ssh-profile "deep-inspection" set nat enable nextFollow me on https://www.linkedin.com/in/yurislobodyanyuk/ not to miss what I publish on Linkedin, Github, blog, and more.

