Recently I had the opportunity to configure an external threat feed as a block list for the Fortigate and was pleasantly surprised by how much simpler it has become. Task at hand: Block incoming connections sourced from IP addresses supplied as a list by a 3rd party commercial Threat Intelligence feed.
Until FortiOS 6.0.1 we had to resort to custom scripting which downloaded those block lists, then parsed and compiled Fortigate CLI commands to add them as address objects, circumventing limitations by grouping addresses into Address Groups. In short, it was doable but painful. But no more - starting with FortiOS 6.0.1 we have a Fabric Connector for the IP address/domains block lists which we can use in DNS Filtering (6.0.1 and newer) and also as regular Address objects in Source/Destination fields of Security Rules (starting with 6.2 and newer).
So let's see how to do it. For this post I will be using free "Bogons List" by Cymru Team as in the original case I was using commercial and confidential one which cannot be disclosed here. The idea is identical - the feed provider gives (usually) HTTP/HTTPS link to download IP block list. The list has to have IP address/network or domain per line and it must be readable as a plain text. Example:
# last updated 1595753401 (Sun Jul 26 08:50:01 2020 GMT)0.0.0.0/85.44.248.0/215.57.208.0/215.172.176.0/21The FortiOS used here is 6.2.3. We start by creating new Fabric Connector: Security Fabric -> Fabric Connectors -> Create New -> Threat Feeds: IP Address. In which we specify URL to download the block list, with optional Basic HTTP Authentication. It should look like this:
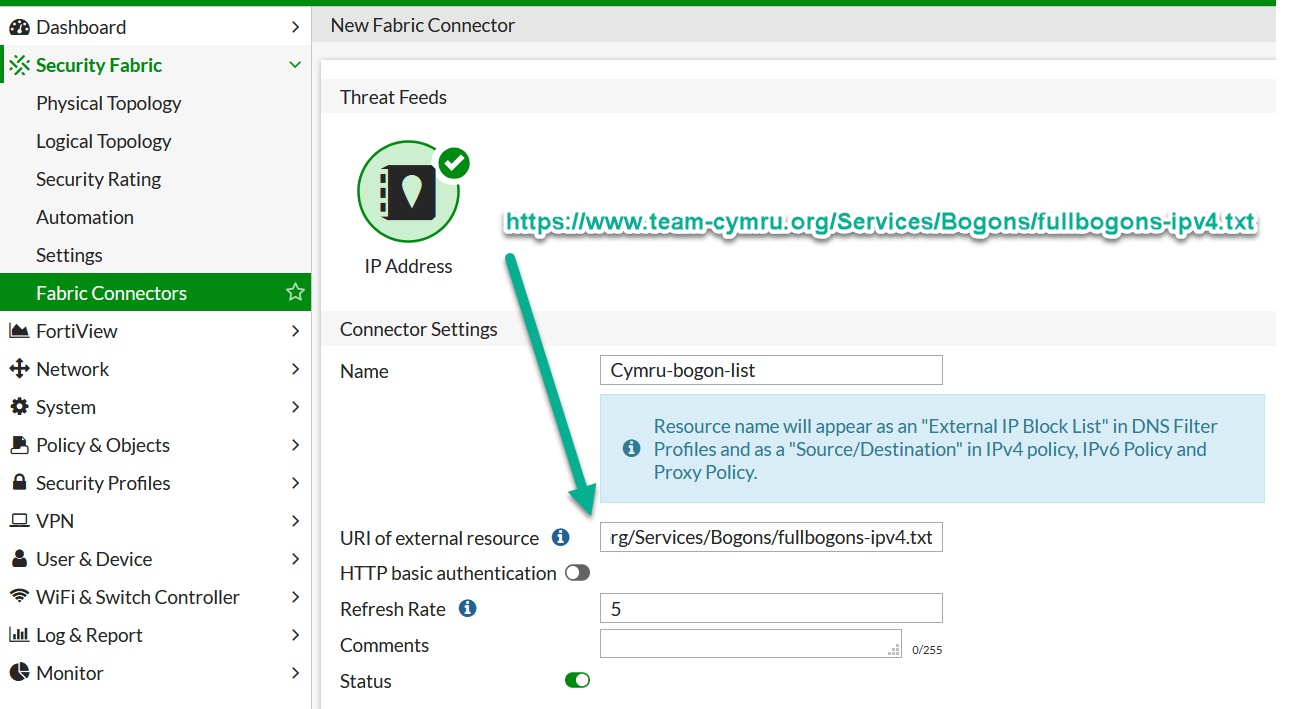
Upon saving, give it few minutes for the Fortigate to fetch the URL. When it is ready, the arrow will change from red to green:
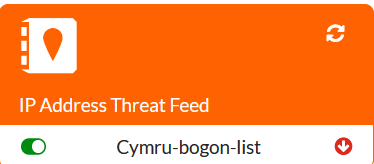
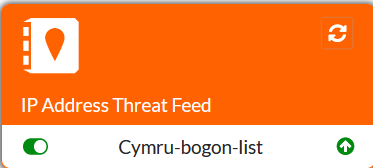
Once the Fabric Connector is synchronized with the feed, we can edit it to verify IPs/domains it downloaded:
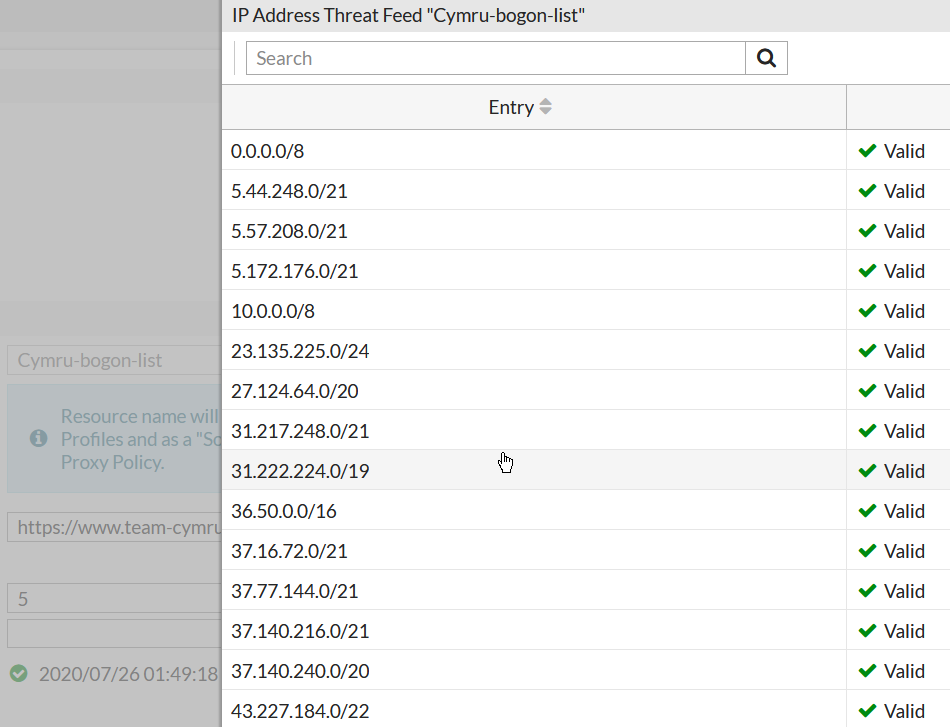
What is left is to use this feed object in Security rule. Here I will create a new rule above the rule allowing HTTP/HTTPS access to the website with the action of Deny:
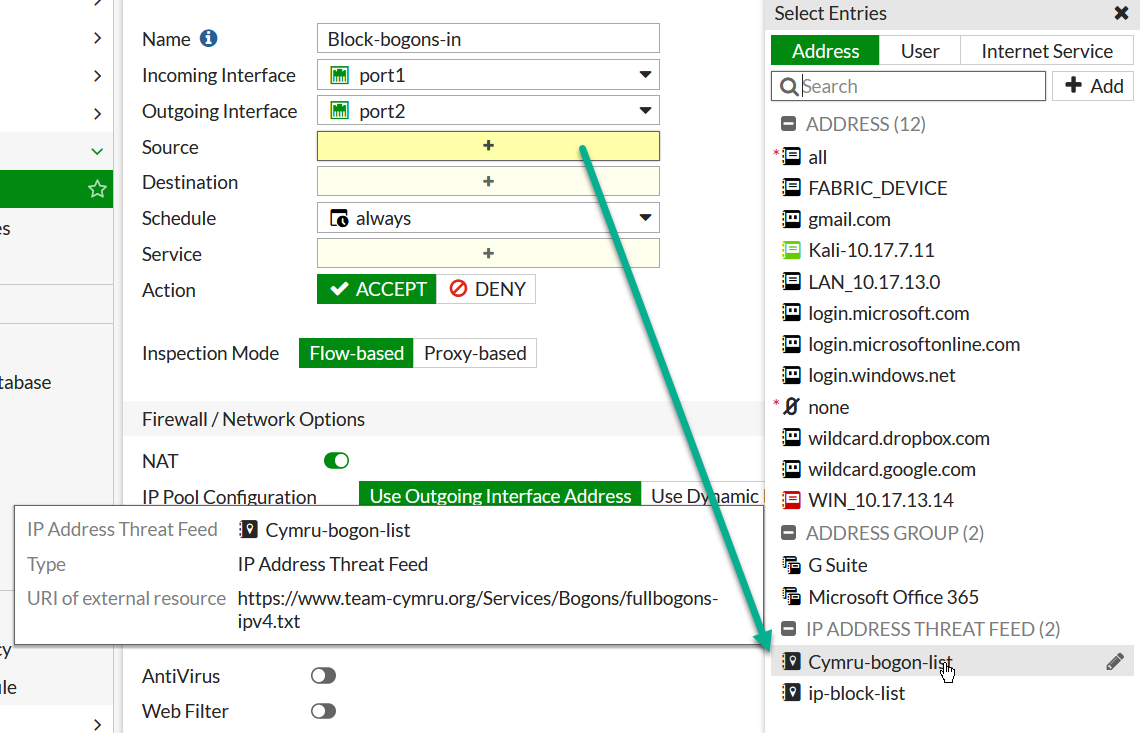
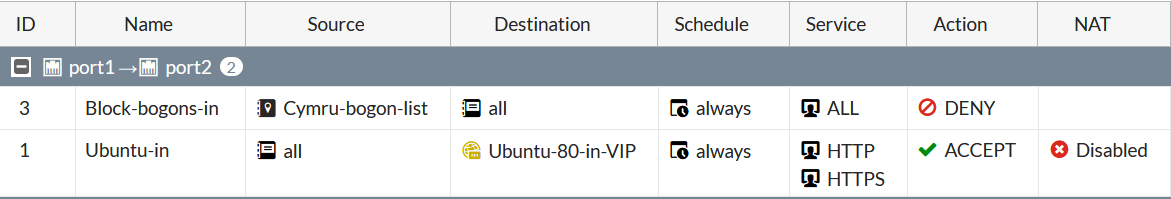
Key takeaway today - keep abreast of new major and minor FortiOS releases, as any update may introduce new feature that will make your life as Network/Security admin much easier.
Resources
Follow me on https://www.linkedin.com/in/yurislobodyanyuk/ not to miss what I publish on Linkedin, Github, blog, and more.

