In an era where digital identities have become the new security perimeter, organizations face an unprecedented challenge. With work no longer limited to the office and employees working from anywhere, coupled with accelerated digital transformation, this has led to an expanded attack surface and heightened cybersecurity risks. Today, a single compromised credential or a malicious insider can spell disaster for even the most robust enterprises. This is where identity threat detection and response (ITDR) emerges as a critical pillar of modern cybersecurity strategy.
Challenges and Cybersecurity Risks
Looking at the challenges security teams currently face, it can seem like a daunting problem to solve:
- Complex Threat Landscape – Organizations face sophisticated cyberattacks targeting identities, making it challenging to detect and respond to threats in real-time.Fragmented Security Solutions – Many organizations use multiple security solutions that do not communicate effectively, leading to security gaps.Increasing Compliance Requirements – Regulatory standards require stringent security measures and detailed reporting, making the management of identity security more complex and challenging.Operational Inefficiencies: Manual threat detection and response processes can lead to delays and human errors, impacting the organization’s overall security posture.
Modern ITDR needs to go beyond traditional identity and access management by leveraging the power of Palo Alto Networks Precision AI, machine learning and automation to provide a continuous, holistic view of identity-related risks. It's not just about who has access, but how that access is being used or misused.
From detecting anomalous login patterns and potential account takeovers to identifying insider threats and session hijacking attempts, ITDR serves as a vigilant guardian of your organization's digital identities.
With these capabilities in mind, imagine this world:
- A disgruntled employee's suspicious file transfers are flagged in real-time, preventing data exfiltration before it occurs.A hacker's attempt to leverage stolen credentials is thwarted before they gain access to sensitive systems, thanks to real-time behavioral analysis.Unusual login patterns from multiple geographic locations trigger immediate alerts and step-up authentication, stopping account takeover attempts in their tracks.Excessive privileged access activities are detected and investigated promptly, mitigating the risk of insider threats.Automated responses instantly revoke access when a user exhibits high-risk behavior, such as attempting to access restricted resources or violating security policies.
These scenarios aren't futuristic concepts but present-day realities enabled by advanced ITDR solutions, like the Cortex Identity Threat Detection and Response module from Palo Alto Networks.
The true power of Cortex’s ITDR is unleashed when integrated with robust identity platforms, such as Okta Identity Cloud, CyberArk, Microsoft Entra ID, PingOne and others. These partnerships create a comprehensive identity protection framework that spans the entire attack lifecycle, from detection to prevention and response. By combining Cortex's advanced threat detection capabilities with third-party Identity Threat Protection platforms, organizations can implement a risk-based approach to user access across all enterprise applications, ensuring that potential threats are mitigated as early as possible.
Understanding the Value of Cortex ITDR Module
Cortex ITDR leverages Precision AI and machine learning to provide a continuous, holistic view of identity-related risks. From detecting anomalous login patterns and potential account takeovers to identifying insider threats and session hijacking attempts, ITDR serves as a vigilant guardian of your organization's digital identities. The Cortex ITDR module, available in Palo Alto Networks Cortex XDR® and Cortex XSIAM® products, is designed to address complex identity-related threats by providing advanced detection and response capabilities.
Key Features That Make Cortex ITDR a Leader in Identity Security:
Behavioral Analytics and Machine Learning – Cortex ITDR utilizes machine learning to analyze user behavior and detect anomalies that may indicate compromised identities. This proactive approach helps identify threats before they can cause significant damage.
Automated Threat Response – Cortex ITDR offers automated responses to detected threats, reducing the time it takes to mitigate risks. These actions include revoking access, triggering multifactor authentication (MFA), isolating endpoints, and more.
Comprehensive Visibility and Monitoring – By aggregating logs and data from various sources, Cortex ITDR provides a holistic view of identity activities across an organization. This comprehensive visibility is crucial for identifying and responding to potential threats.
Integration with Threat Intelligence – Continuous updates from our Palo Alto Networks threat intelligence feed enhance Cortex ITDR’s ability to detect emerging threats, ensuring that organizations are always protected against the latest attack vectors.
Incident Response and Forensics – Detailed incident analysis and forensics capabilities enable security teams to understand the nature of threats and take appropriate action to prevent future incidents.
Enhancing Cortex ITDR Through Integrations with External Identity Vendors
While Cortex ITDR offers powerful identity security capabilities on its own, its ability to integrate with a diverse range of identity vendors, including Okta and others, elevates these capabilities to the next level. The synergy between these solutions provides several technical benefits:
Real Time Data Ingestion and Analysis – External identity data is seamlessly ingested into Cortex XDR® and Cortex XSIAM®, enabling the ITDR module to provide real-time analysis and threat detection. This integration ensures that any suspicious activity is immediately identified and addressed.
Automated Threat Mitigation – Detected threats in Cortex ITDR can trigger automated security actions on integrated Identity solutions, such as enforcing MFA, preventing access or prompting users for additional verification. This automation enhances response times and reduces the risk of human error.
Unified Dashboard for Enhanced Visibility – Security teams can monitor and manage identity security through unified dashboards, improving operational efficiency and providing a comprehensive view of potential threats and incidents.
Proactive Threat Hunting and Incident Response – The combined solution enables security teams to proactively hunt for identity threats using advanced analytics and threat intelligence, while detailed incident response capabilities help mitigate risks more effectively.
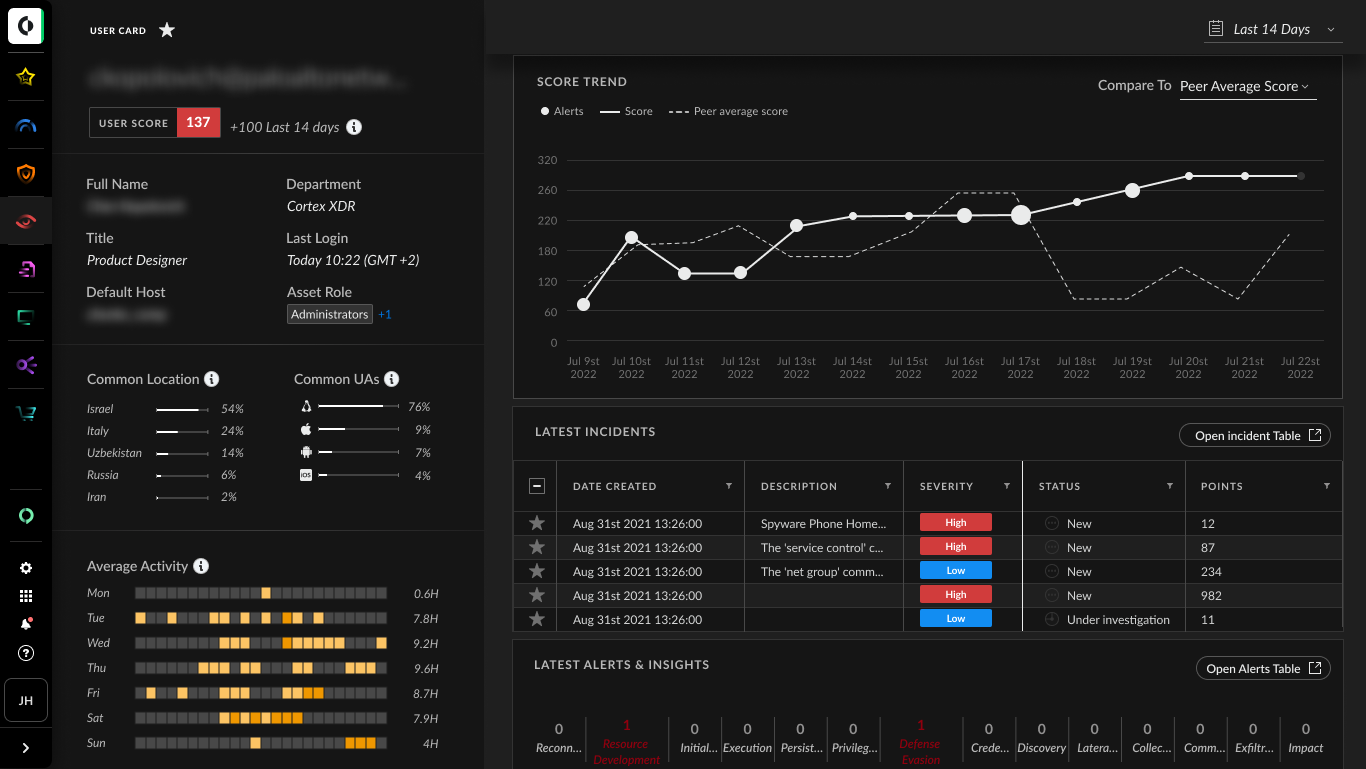
Use Cases
Detecting and Mitigating Compromised Accounts: Cortex ITDR’s behavioral analytics detect unusual login patterns or access attempts, triggering automated responses to secure compromised accounts and prevent unauthorized access. This real-time detection and response capability significantly reduces the window of opportunity for attackers, minimizing potential damage from account takeovers and protecting sensitive data and systems from exploitation.
Preventing Insider Threats: Cortex ITDR identifies anomalies in user behavior that may indicate insider threats. Automated actions, such as revoking access or increasing authentication requirements, help prevent data breaches. By continuously monitoring user activities and comparing them against established baselines, the integrated solution can quickly flag and respond to suspicious behaviors, even from trusted users, thereby safeguarding against both malicious and inadvertent insider threats.
Streamlined Compliance Reporting: The integration helps organizations meet regulatory requirements by providing detailed logs and reports on identity activities and security incidents, simplifying compliance reporting. This comprehensive documentation not only satisfies auditor requirements but also provides valuable insights for continuous improvement of security policies and practices, helping organizations stay ahead of evolving compliance standards.
Enhancing Operational Efficiency: The unified management and automated responses reduce the workload on security teams, allowing them to focus on strategic security initiatives and proactive threat management. By automating routine tasks and providing a centralized view of identity-related security events, the integrations empower security teams to respond more quickly to critical threats, conduct more thorough investigations, and develop more effective long-term security strategies.
Benefits of the Joint Solution
By leveraging these integrated solutions, organizations can shift from a reactive to a proactive security posture. The AI-driven approach allows for the anticipation and prevention of threats before they materialize, significantly reducing the risk of data breaches and other security incidents. This not only enhances security but also frees up valuable resources, allowing security teams to focus on strategic initiatives rather than constant firefighting, putting the “pro” in proactive.
For organizations utilizing the powerful integrations available with Cortex ITDR, the benefits are multifaceted:
Robust Security Posture – The integrations provide a comprehensive security framework that significantly enhances an organization’s ability to detect and respond to identity threats, ensuring a stronger security posture. Combining Cortex ITDR's advanced threat detection capabilities with robust identity management platforms, organizations can create a multilayered defense that addresses the full spectrum of identity-related risks, from credential compromise to insider threats.
Operational Efficiency and Automation – Automation and unified management streamline security operations, reducing the time and effort required to manage identity security and respond to incidents. This enhanced efficiency allows security teams to focus on strategic initiatives rather than routine tasks, ultimately improving the overall effectiveness of the security program and reducing response times to critical threats.
Regulatory Compliance Made Easier – The integration simplifies compliance reporting, helping organizations meet regulatory requirements more efficiently and with greater accuracy. With comprehensive logging and reporting capabilities, organizations can easily demonstrate their security measures and incident response protocols to auditors, reducing the stress and resource drain typically associated with compliance audits.
Future-Proof Security – Continuous updates and advancements in threat intelligence from Palo Alto Networks ensure that organizations remain protected against the latest threats, providing peace of mind and long-term security. This adaptive approach to security means that as new attack vectors and techniques emerge, the integrated solutions evolve to counter them, keeping organizations one step ahead of potential adversaries and reducing the risk of falling victim to novel cyberthreats.
Conclusion — More Secure, More Efficient, More Compliant
By integrating advanced identity threat detection and response capabilities from Cortex with robust identity management solutions, such as Okta, CyberArk and others, organizations can achieve a more secure, efficient and compliant security posture. This integration not only addresses the complex challenges of today’s threat landscape but also empowers organizations to stay ahead of cyber adversaries with confidence.
Read this solution brief or this blog to learn more about Cortex ITDR.
The post Identity Protection That Spans the Entire Attack Lifecycle appeared first on Palo Alto Networks Blog.

