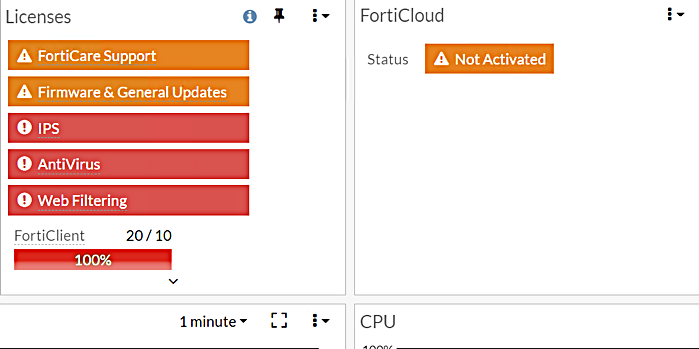
When subscription for Fortiguard-based services expires, many things will stopworking, but a lot will continue to work still. Below is the full list of featuresin Fortigate that will continue working after the subscription expires. Italso means these features work even if your Fortigate has never had thesubscription in the first place.
Warning | VM Fortigate has a license check, which is unrelated to the Fortiguardsubscription. This license check requires a non-stop online communication withthe Fortiguard servers. The VM Fortigate will stop working completely, if itcannot reach Fortiguard servers for a long time (30 days usually), unless usinga special, offline license (most clients don’t). |
Security rules. The Fortigate will continue filteringtraffic according to the Security Rulebase.
All kinds of NAT: SNAT, DNAT, VIP, dynamic pools, etc.
VPN - all types, IPSec site-to-site, Remote Access as SSL VPN in webmode and full tunnel withForticlient and as IPSec client.
IPS with the signatures last updated before the subscription expired. That is,IPS will continue working, but new signatures will not be downloaded.
AppControl using the signatures last updated before the subscription expired.
Web/URL Filtering using static allow/block lists. Without subscriptionthe firewall cannot query FortiGuard for URL web ratings, so Web filtering usingFortiguard assigned Categories will not work. But if you use staticblock/allow URL lists, they will work. Also blocking ActiveX controls will worktoo.
All types of interfaces: physical, VLANs, Virtual Wire, Loopbacks, LAGs,redundant, Zones.
Security rules modes: proxy and flow. All modes of proxy mode will work: Explicit, Transparent.
SSL/SSH inspection - certificate and deep packet inspection.
Applying UTM in both: Policy based and Profile based modes.
VDOMs.
High Availability (HA).
QOS.
SD-WAN feature, including AppControl integration (but see above aboutApplication Control signature updates).
WAF with the signatures last updated before the subscription expired.
VIP of load balancing type.
DoS/DDoS protection rules.
Device inventory.
Access Point controller.
FortiSwitch management.
All types of logging, Netflow/sFlow export.
GRE and VXLAN traffic encapsulation.
VRFs, if supported by FortiOS version.
One-arm sniffer.
Static, all dynamic protocol, and Policy Based routing.
All types of authentication: local, LDAP, Radius, Tacacs, SAML, MFA.
SNMP.
DHCP server.
Internet Service Database (ISDB).
External Threat Feeds.
VOIP protections and profiles.
Configuration version revisions.
DLP.
Additional Resources
Follow me on https://www.linkedin.com/in/yurislobodyanyuk/ not to miss what Ipublish on Linkedin, Github, blog, and more.

