AWS Guide to Cloud Architecture Diagrams (Sponsored)
Enhance visibility into your cloud architecture with expert insights from AWS + Datadog. In this ebook, AWS Solutions Architects Jason Mimick and James Wenzel guide you through best practices for creating professional and impactful diagrams.
This week’s system design refresher:
JWT Simply Explained
The 5 Pillars of API Design
How Computer Memory Works?
Top Kubernetes Scaling Strategies You Must Know
Hiring Now: Top AI Startups and AI Roles
SPONSOR US
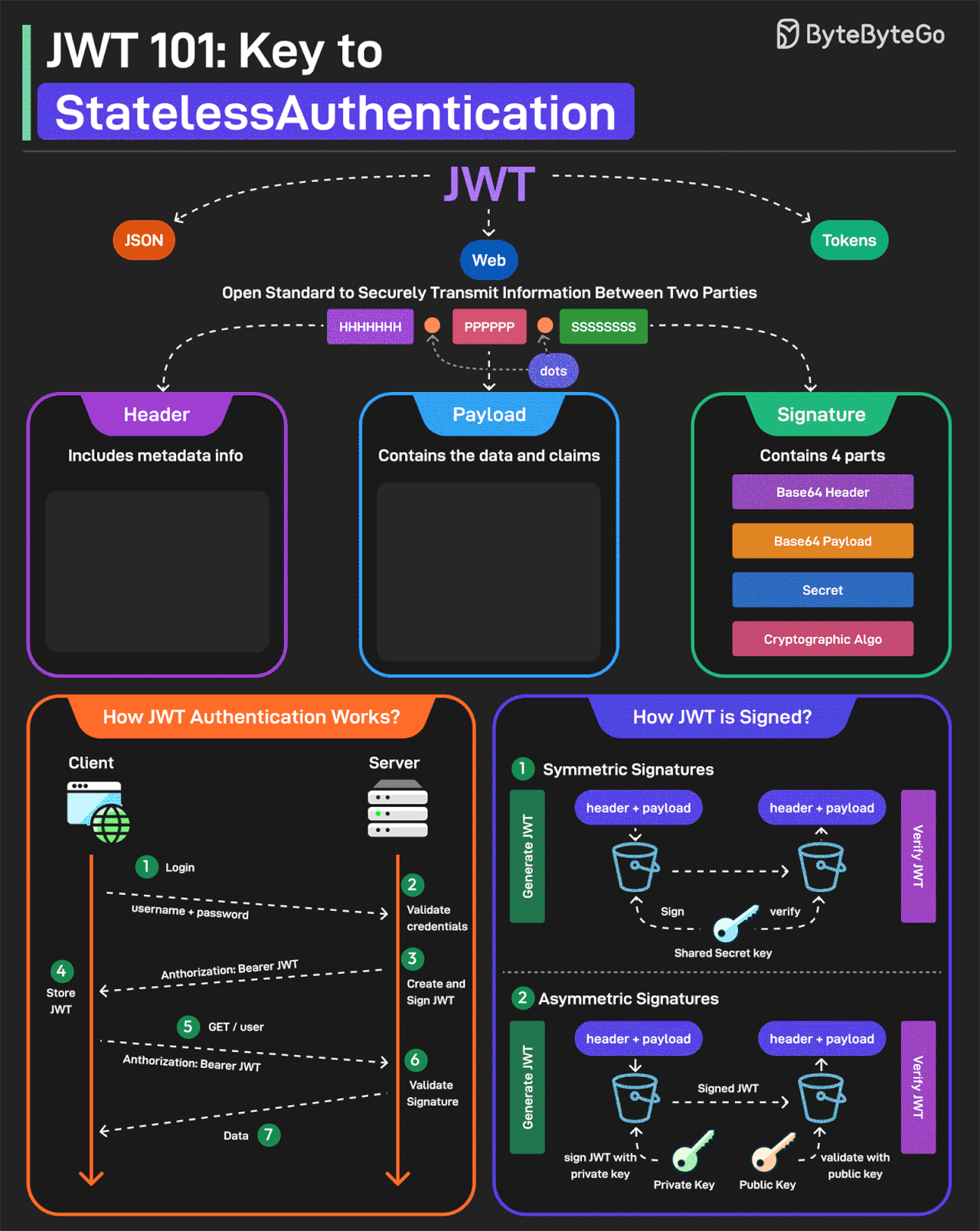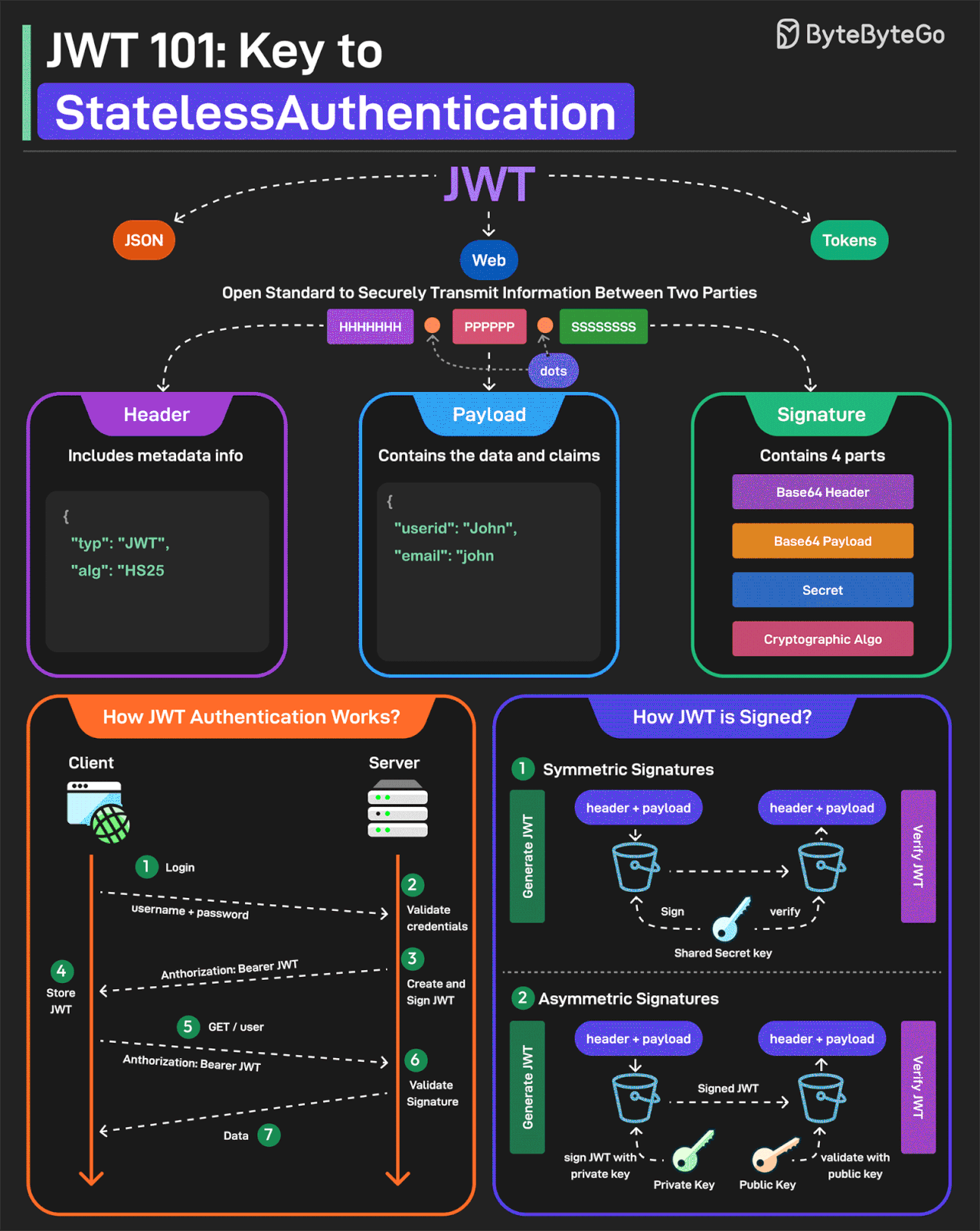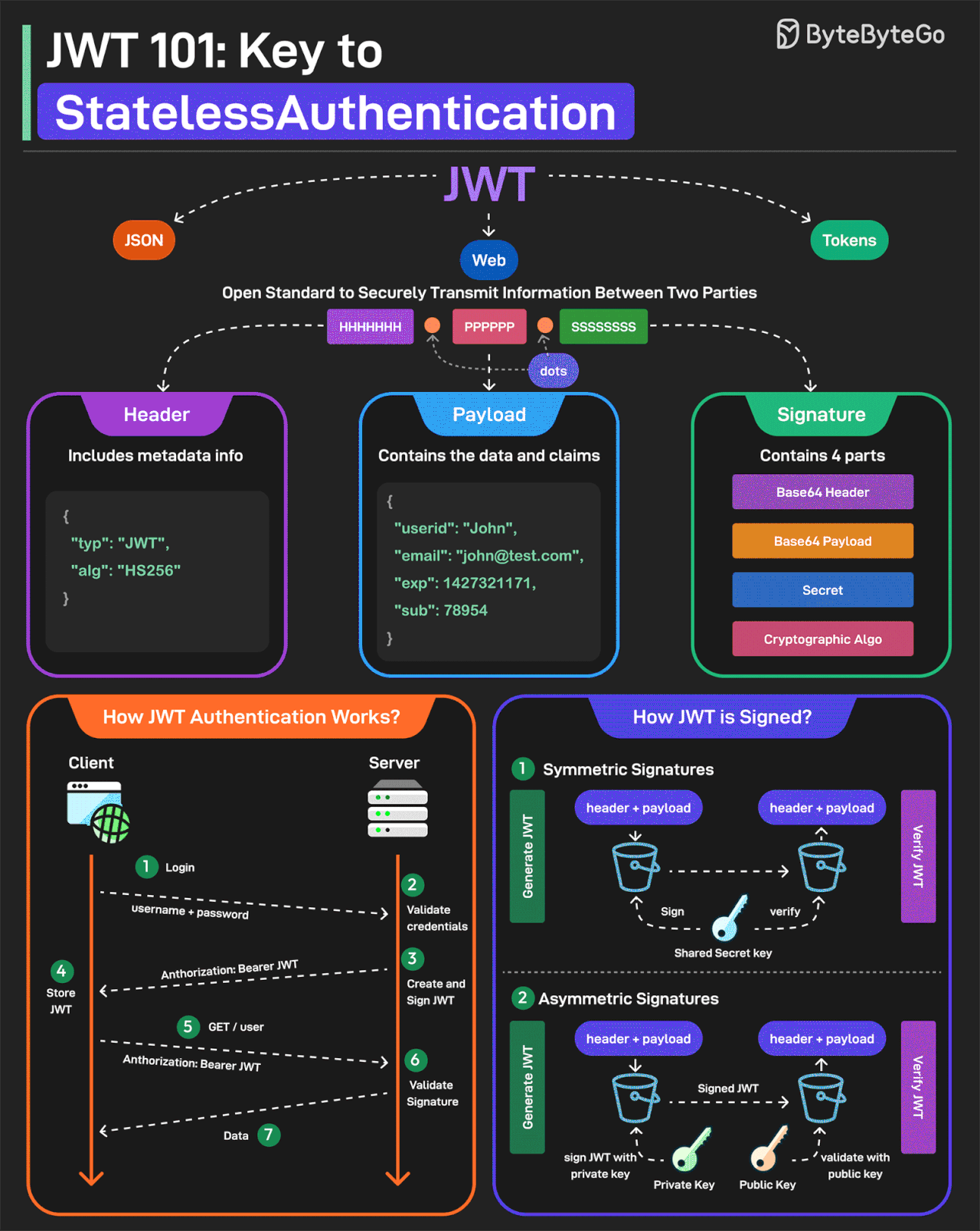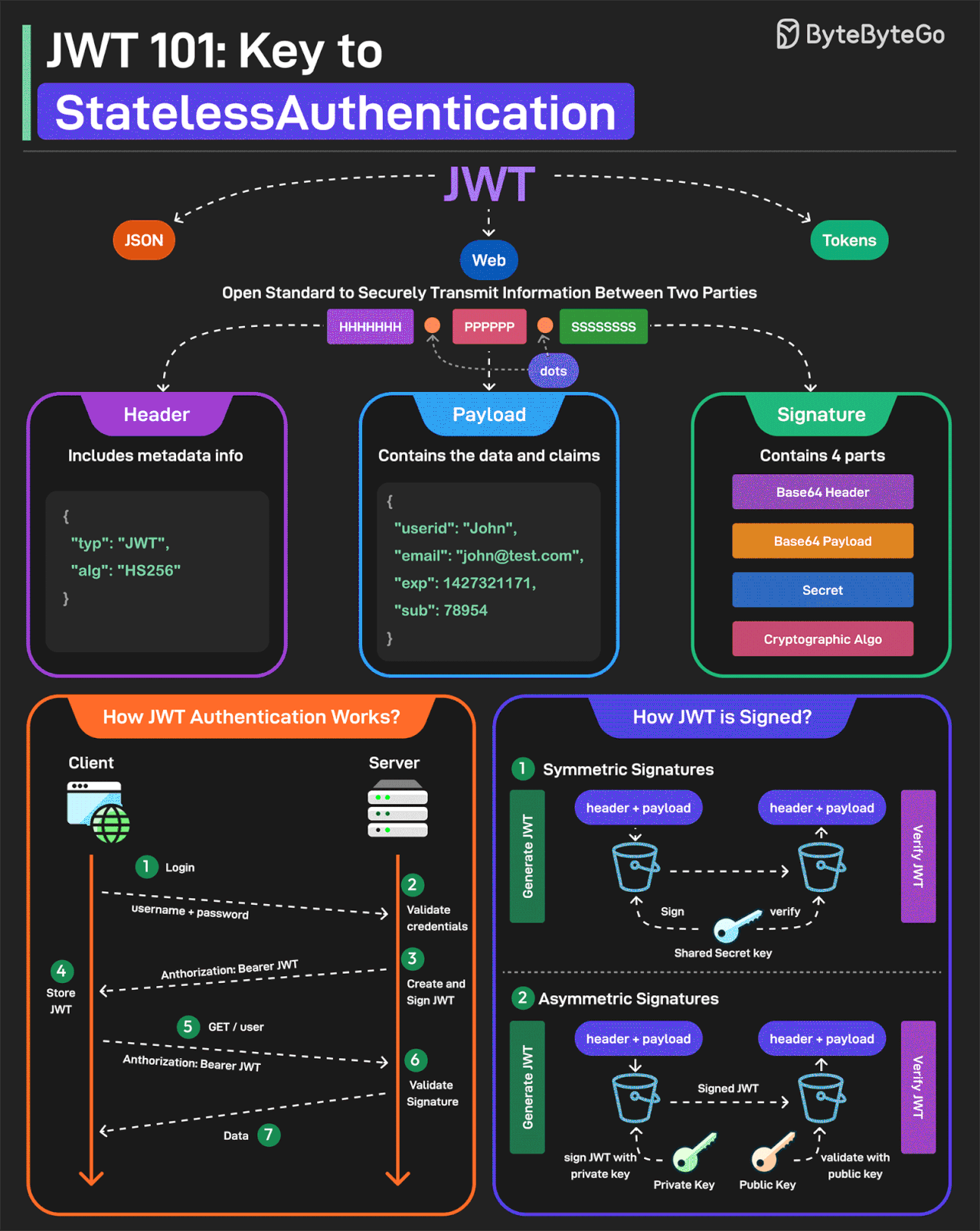
JWT Simply Explained
JWT or JSON Web Tokens is an open standard for securely transmitting information between two parties. They are widely used for authentication and authorization.
A JWT consists of three main components:
Header
Every JWT carries a header specifying the algorithms for signing the JWT. It’s written in JSON format.
Payload
The payload consists of the claims and the user data. There are different types of claims such as registered, public, and private claims.
Signature
The signature is what makes the JWT secure. It is created by taking the encoded header, encoded payload, secret key, and the algorithm and signing it.
JWTs can be signed in two different ways:
Symmetric Signatures
It uses a single secret key for both signing the token and verifying it. The same key must be shared between the server that signs the JWT and the system that verifies it.
Asymmetric Signatures
In this case, a private key is used to sign the token, and a public key to verify it. The private key is kept secure on the server, while the public key can be distributed to anyone who needs to verify the token.
Over to you: Do you use JWTs for authentication?
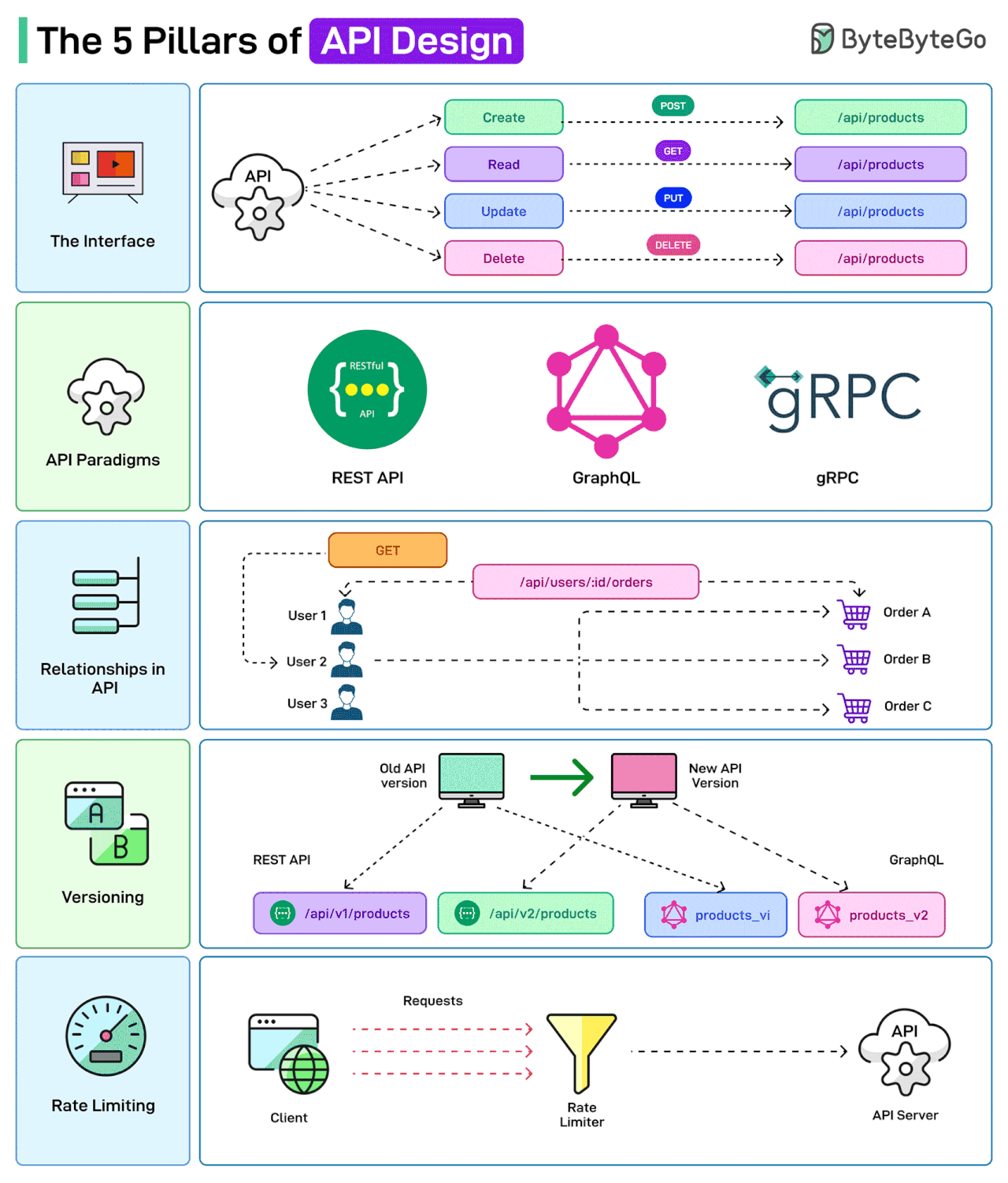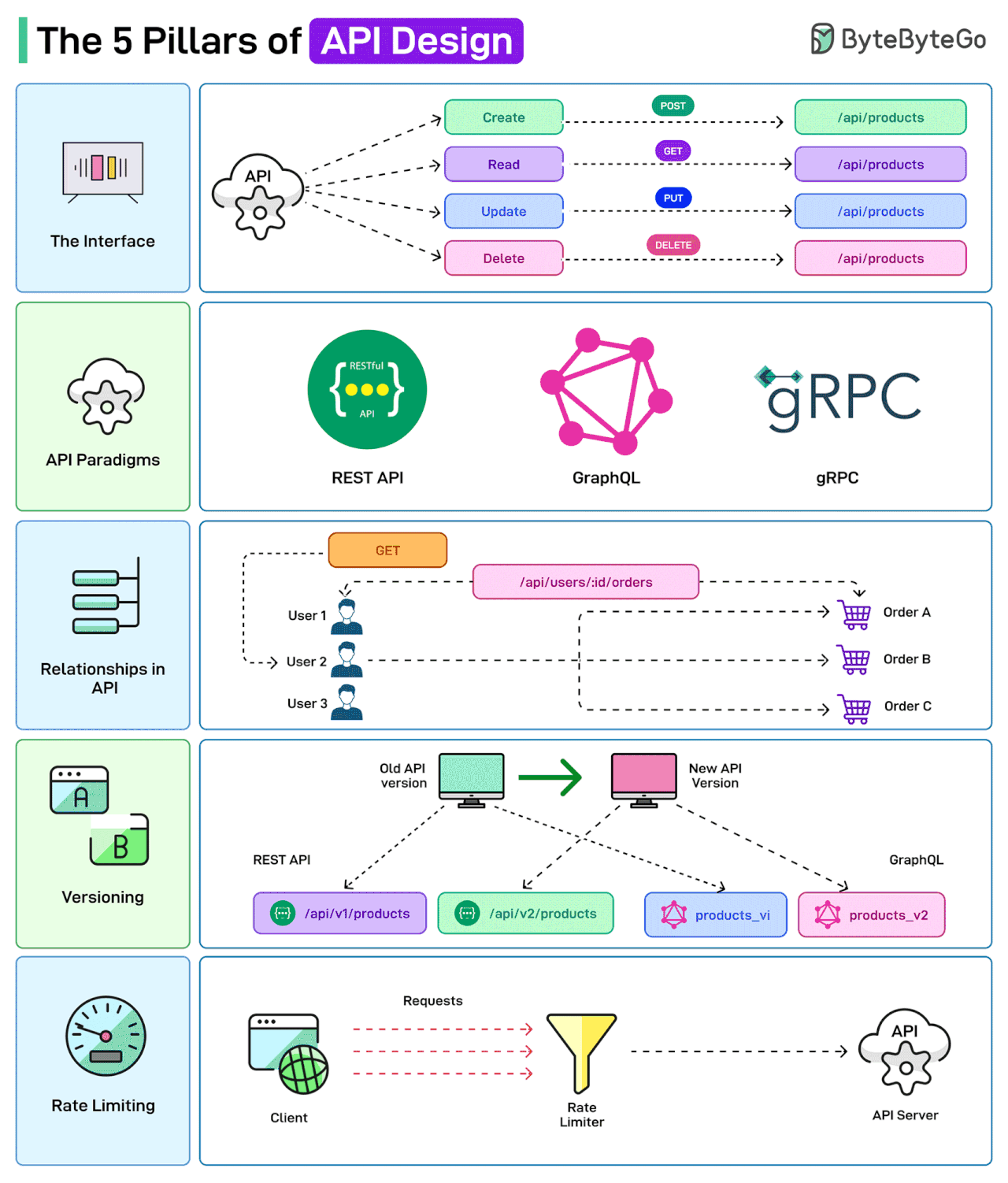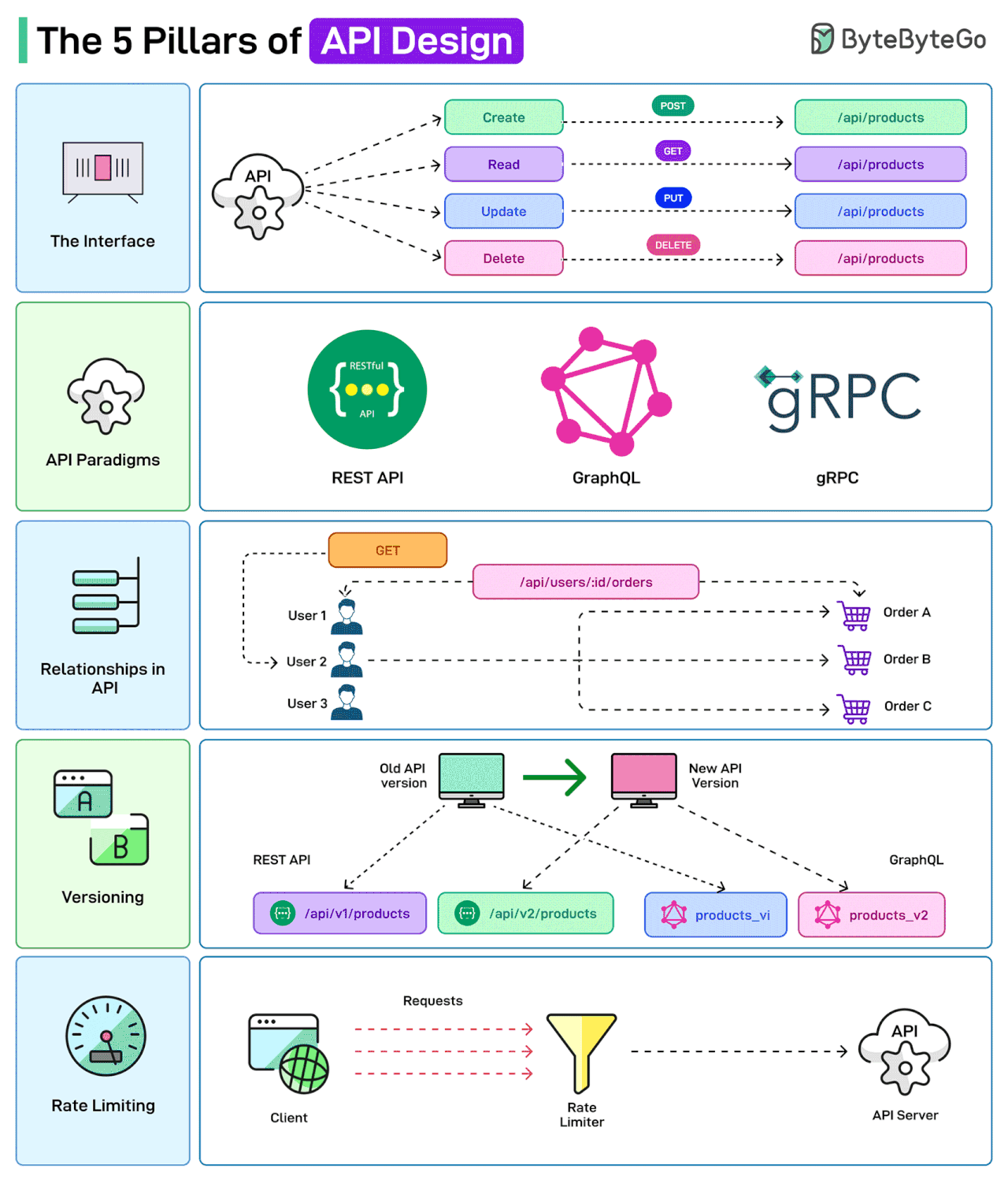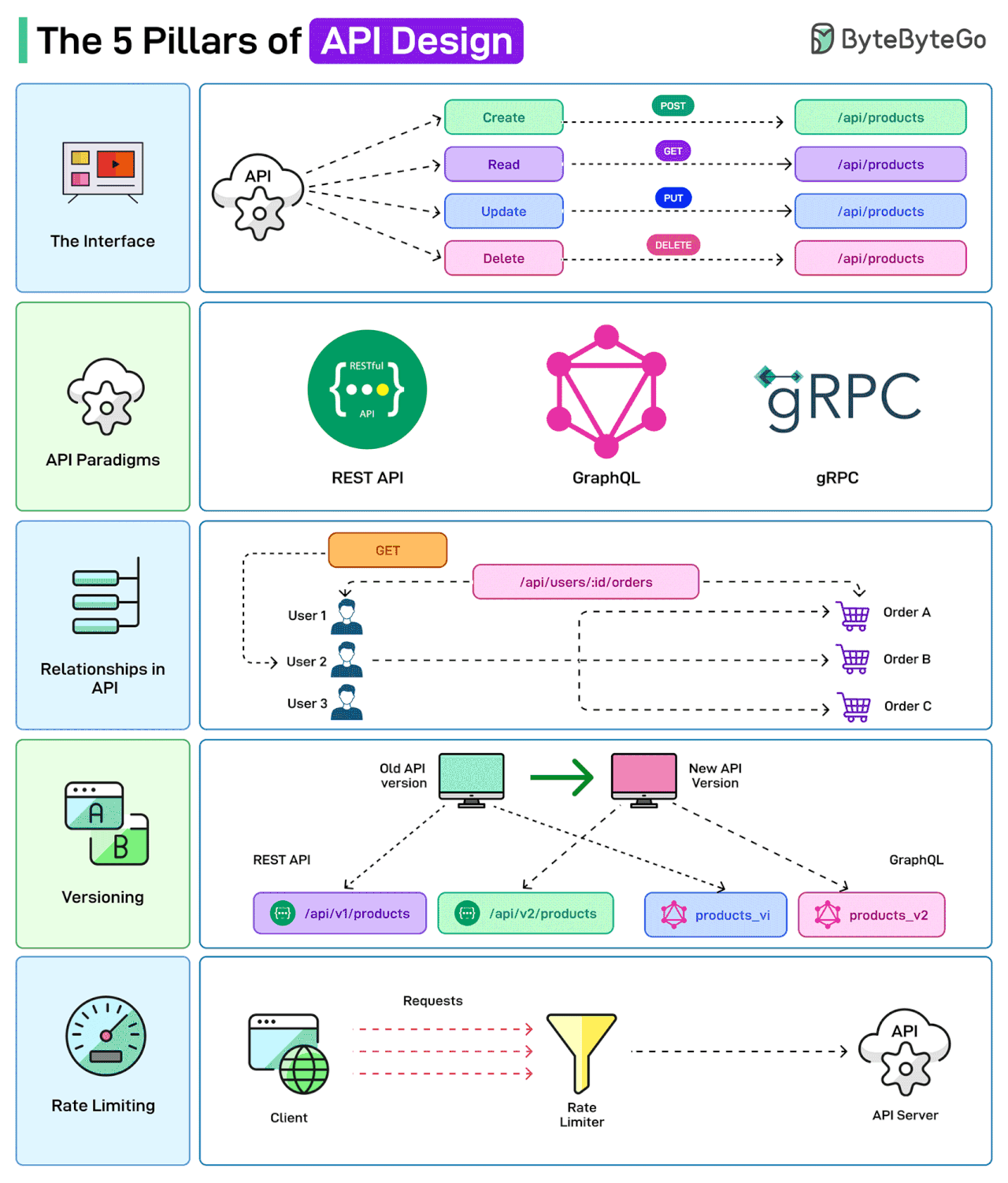
The 5 Pillars of API Design
APIs are the backbone of modern systems. But it is also important to design them in the right way.
Here are a few things that a developer should consider while designing APIs
The Interface
API Design is concerned with defining the inputs and outputs of an API. For example, defining how the CRUD operations may be exposed to the user or the client.
API Paradigms
APIs can be built following different paradigms, each with its own set of protocols and standards. Some options are REST, GraphQL, and gRPC.
Relationships in API
APIs often need to establish relationships between the various entities. For example, a user might have multiple orders related to their account. The API endpoints should reflect these relationships for a better client experience.
Versioning
When modifying API endpoints, proper versioning and supporting backward compatibility are important.
Rate Limiting
Rate limiting is used to control the number of requests a user can make to an API within a certain timeframe. This is crucial for maintaining the reliability and availability of the API.
Over to you: Which other API Design principle will you add to the list?
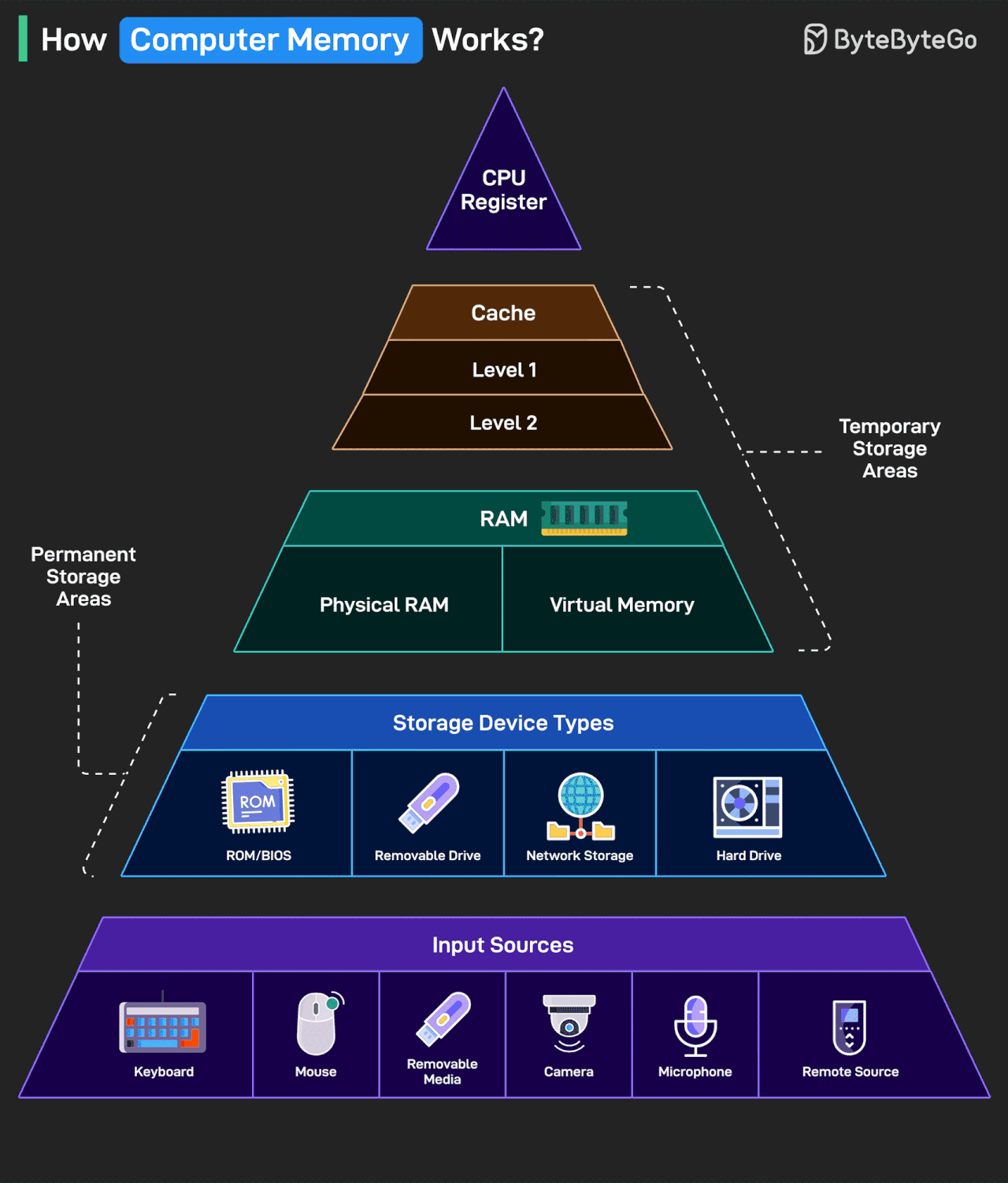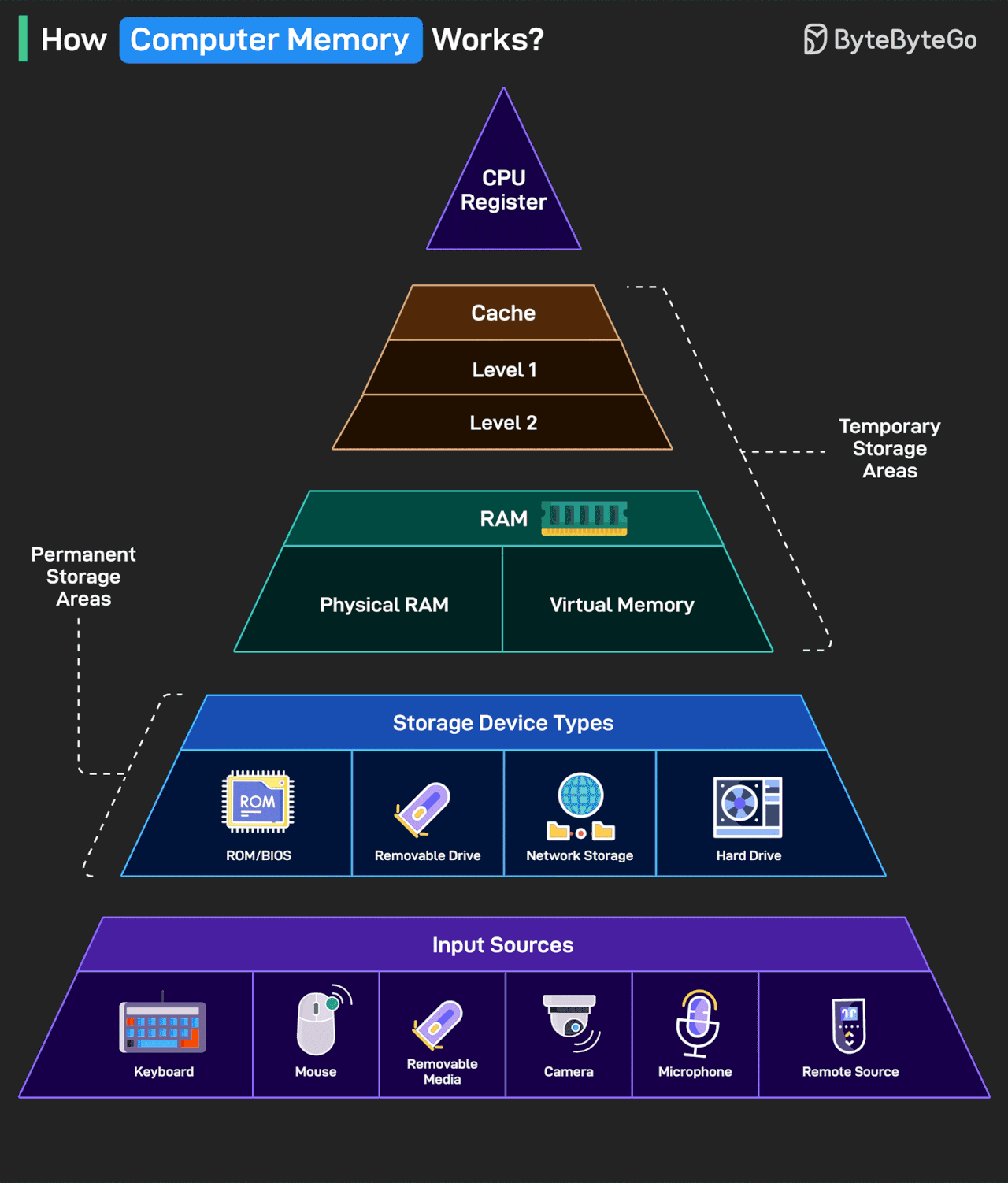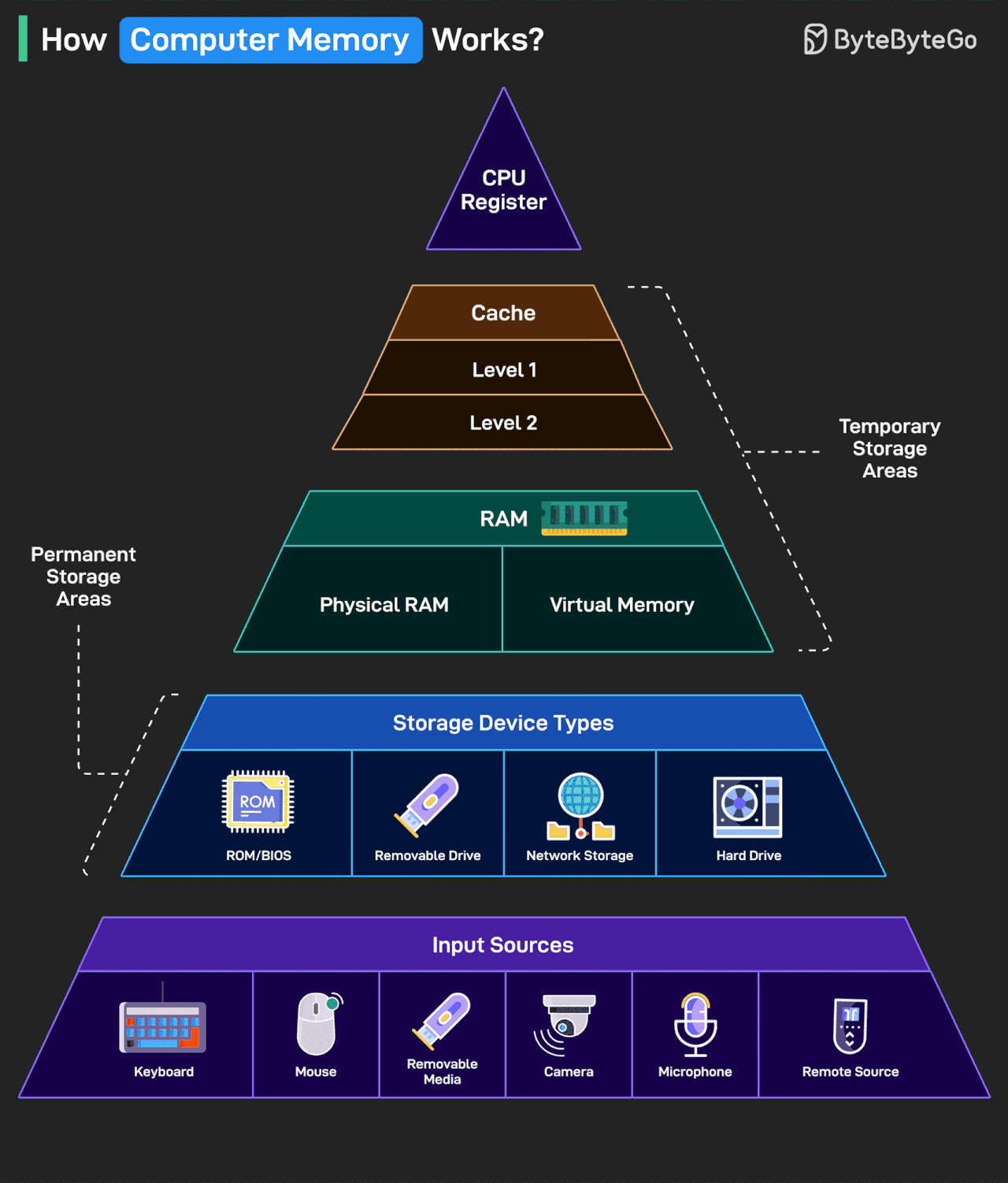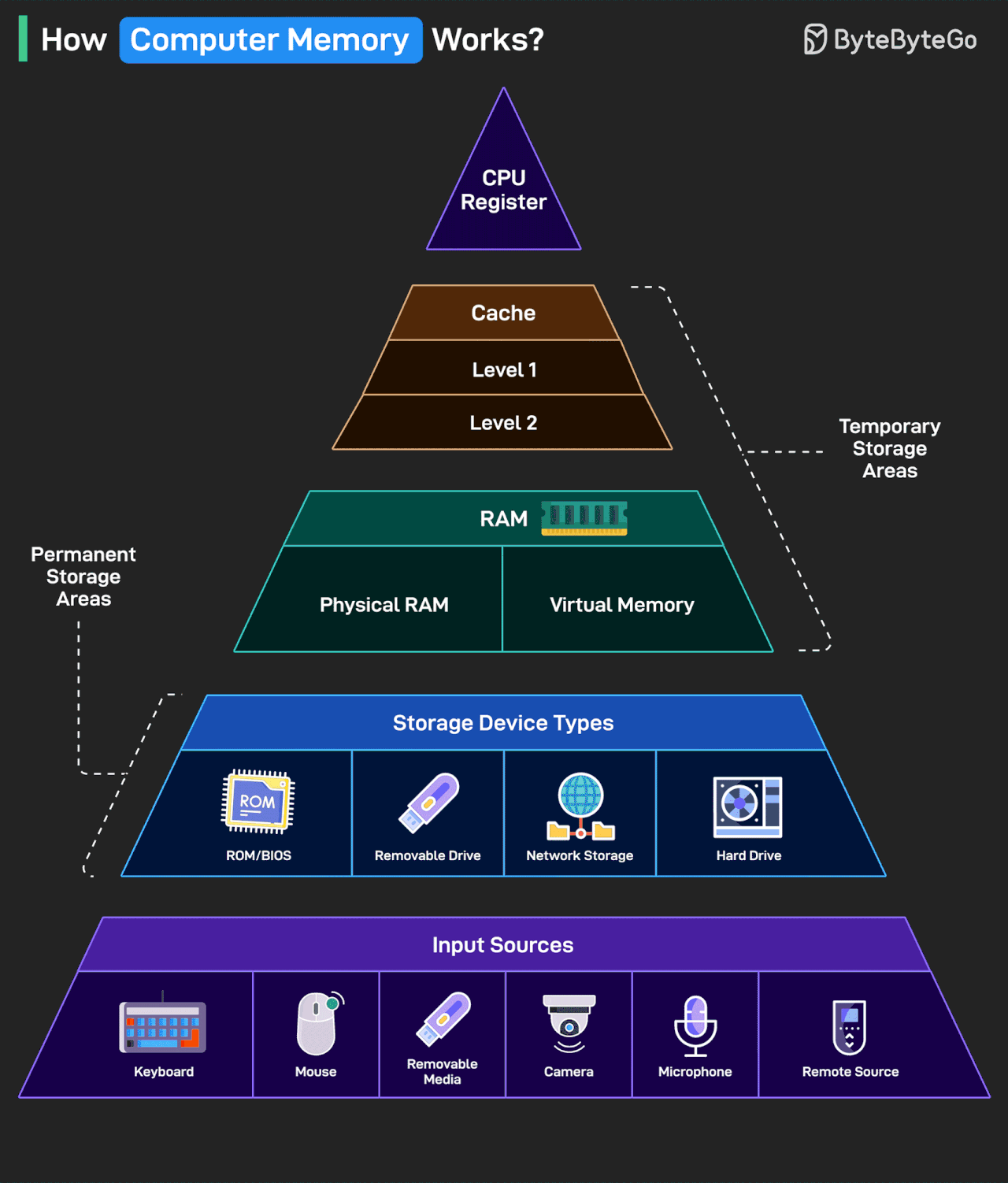
How Computer Memory Works?
Here’s a simple breakdown that shows how data moves through a system from input to processing to storage.
Data enters through input sources like keyboard, mouse, camera, or remote systems.
Permanent storage holds your system files, apps, and media. This includes hard drives, USB drives, ROM/BIOS, and network-based storage.
RAM is the workspace of your computer. It includes physical memory and virtual memory, which temporarily store data and programs while you’re using them.
Cache memory sits closer to the CPU and is split into Level 1 and Level 2. It helps speed up access to frequently used data.
CPU registers are the fastest and smallest memory units. They’re used directly by the processor to execute instructions almost instantly.
The higher you go in the memory pyramid, the faster and smaller the storage.
Over to you: What else will you add to improve the understanding of a computer memory’s working?
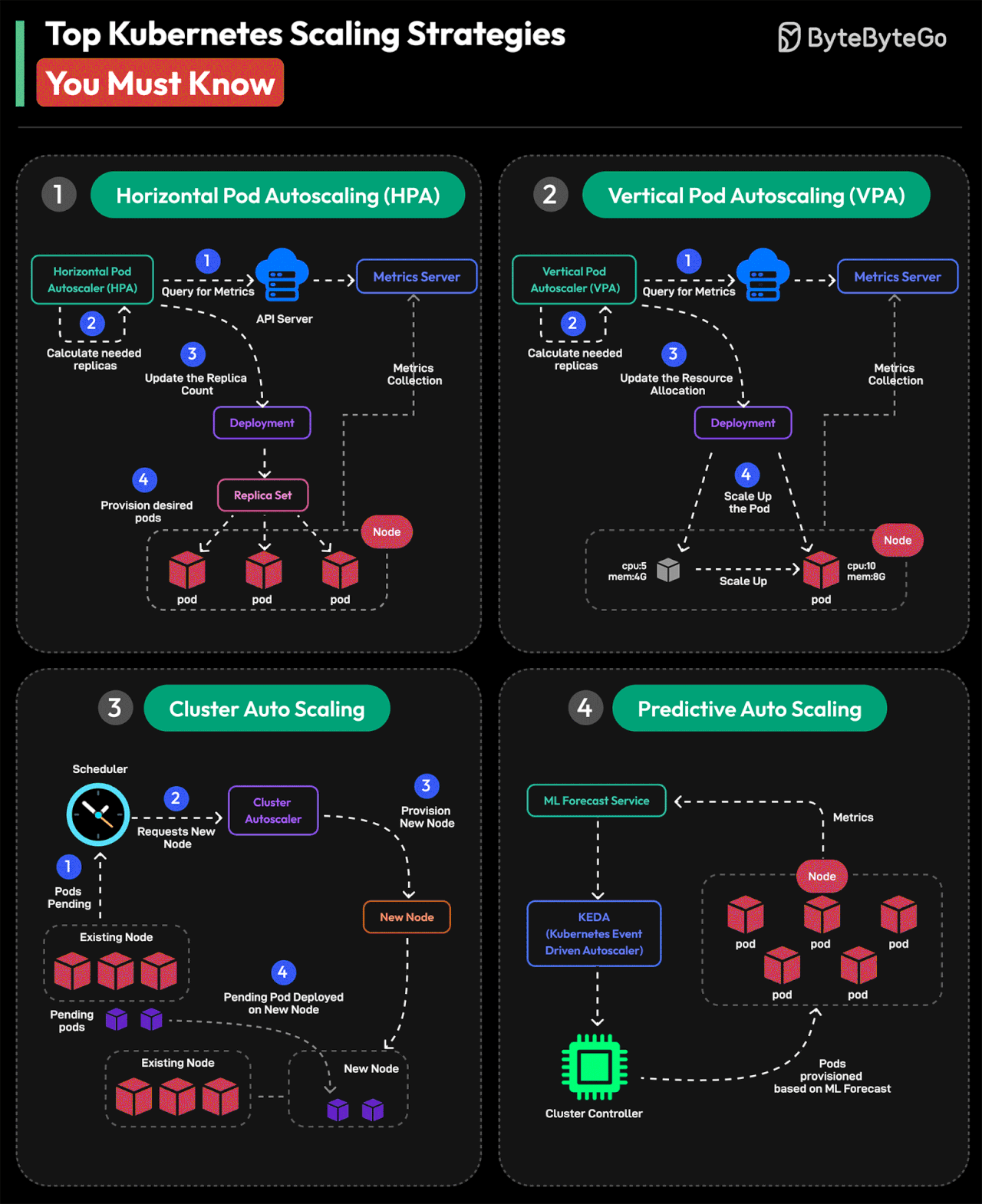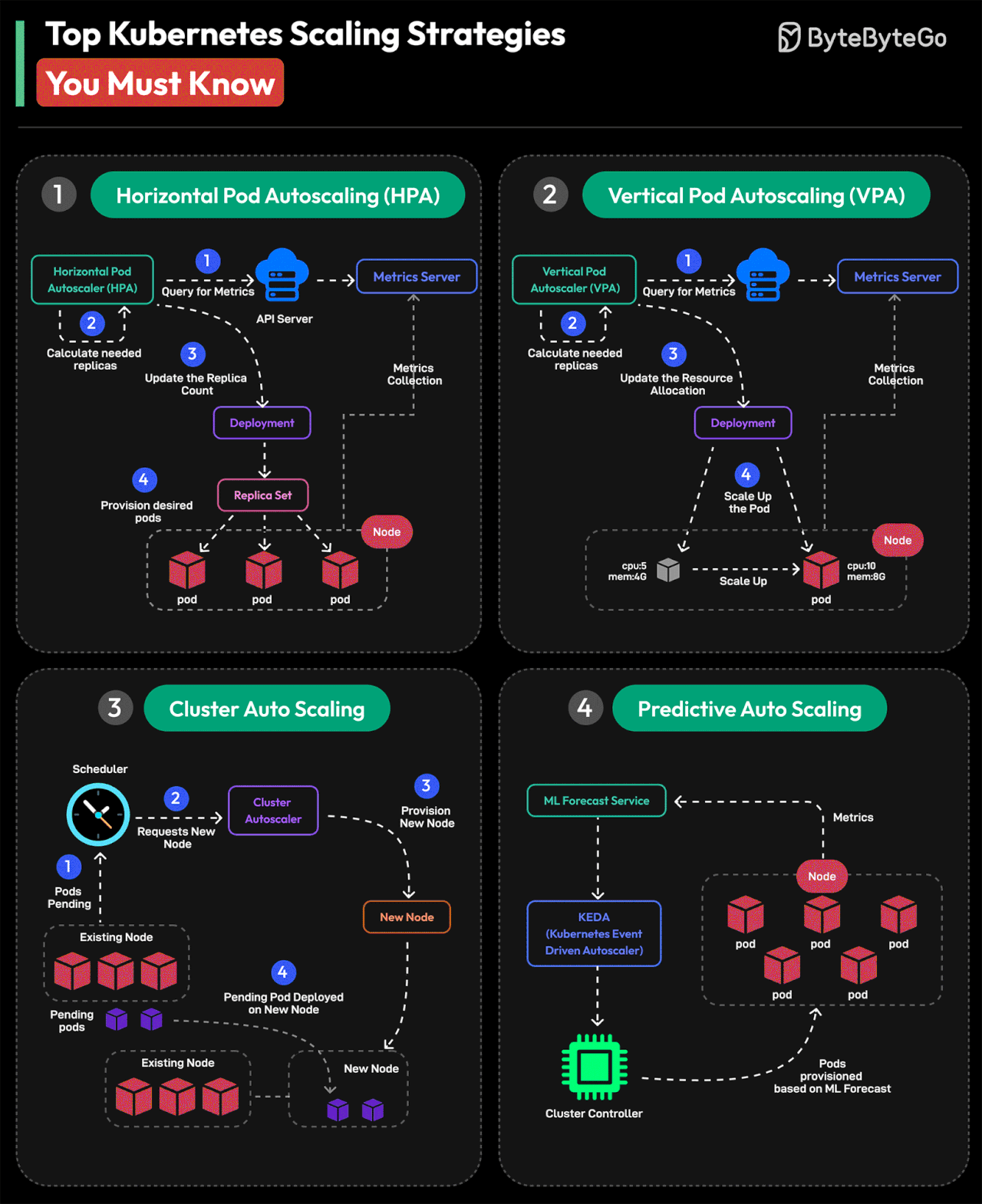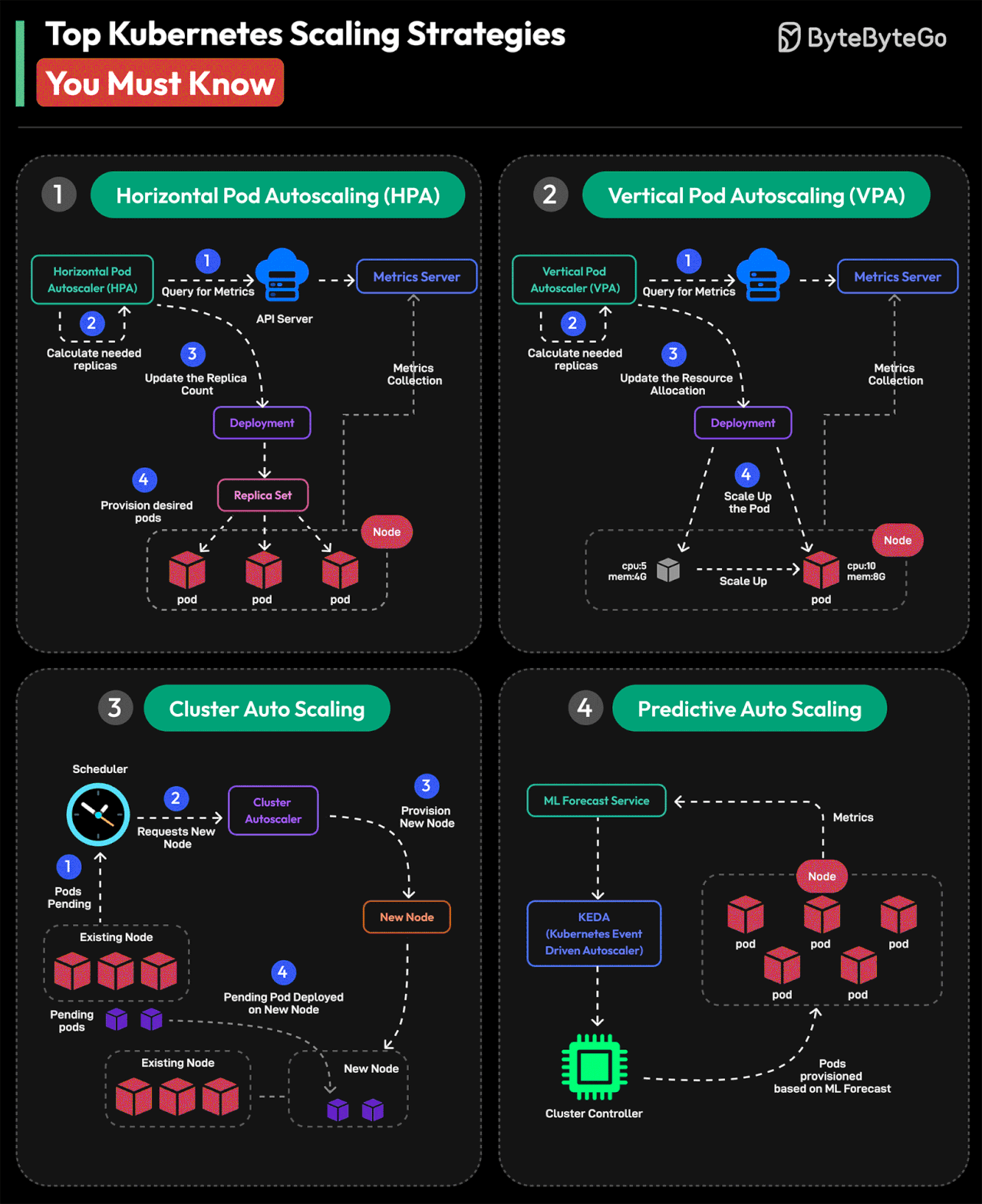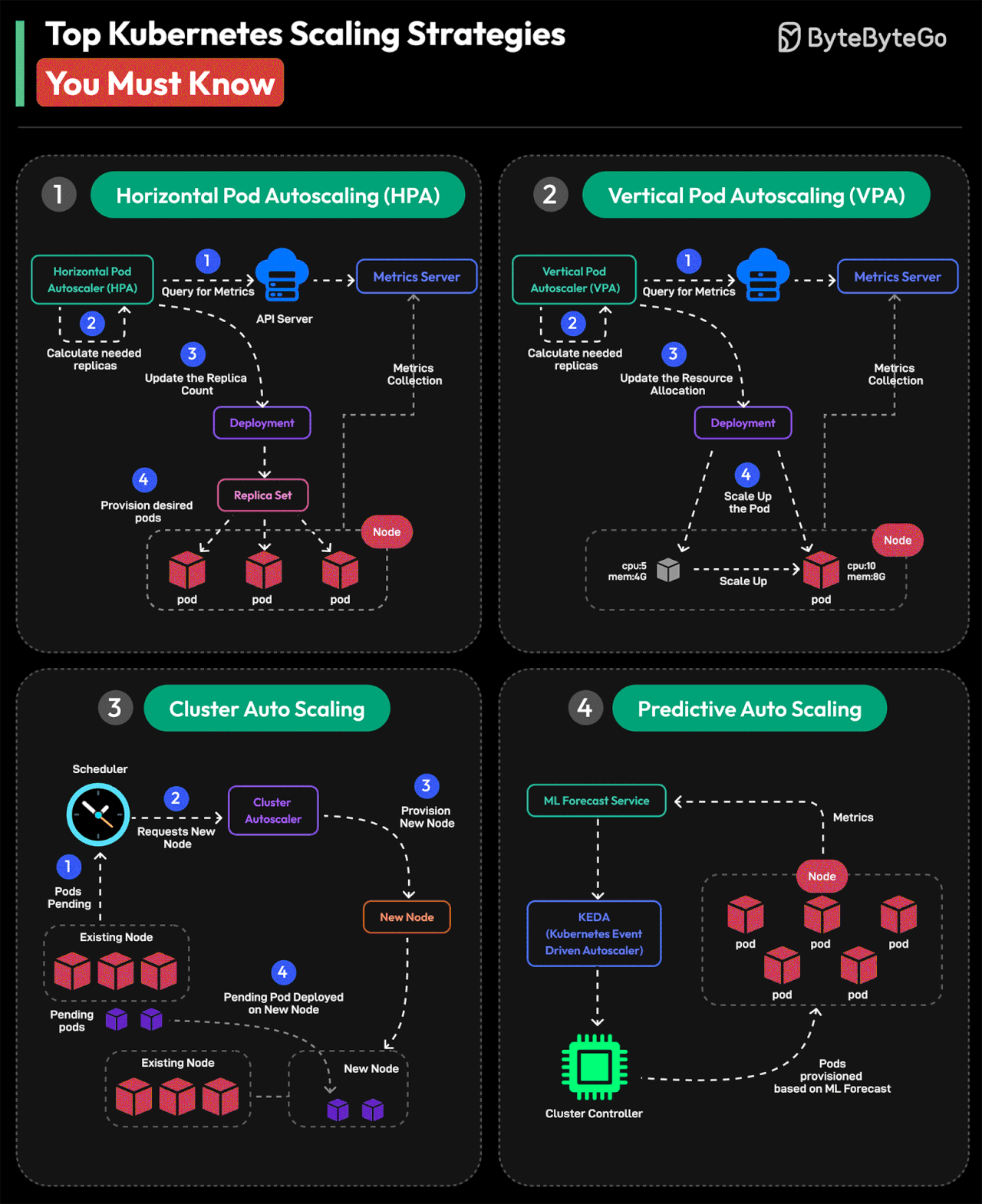
Top Kubernetes Scaling Strategies You Must Know
Horizontal Pod Autoscaling or HPA
Horizontal Pod Autoscaler automatically scales the number of Pods in a Deployment, ReplicaSet, or StatefulSet based on observed CPU utilization, memory usage, or custom metrics.
Vertical Pod Autoscaling or VPA
Based on application requirements, VPA adjusts the resources allocated to individual pods, such as CPU and memory. This approach dynamically changes pod resource settings based on workload metrics.
Cluster Auto Scaling
The Cluster Autoscaler automatically adjusts the number of nodes in a Kubernetes cluster. It interacts with the cloud provider to add or remove nodes based on requirements. This is important to maintain a balanced cluster.
Predictive Auto Scaling
Predictive Autoscaling uses machine learning to forecast future resource requirements. It helps Kubernetes adjust resources by anticipating workload demands.
Over to you: Which other Kubernetes Scaling Strategy will you add to the list?
Hiring Now: Tech Roles
Top ML Roles Opened in the Last 12 Hours
Senior Machine Learning Engineer (Modeling) - Underwriting & Credit at Cash App
Senior Principal Machine Learning Engineer at Roche
Principal Machine Learning Engineer – AI Core Infrastructure at General Motors
Senior Machine Learning Engineer at MD Anderson Cancer Center
Technical Lead, Machine Learning (AI Defense at Cisco
Sr Principal Machine Learning Engineer (GenAI/LLM) at Palo Alto Networks
Senior Machine Learning Engineer at Adobe
AI/Machine Learning Analyst Lead at Peraton
High Impact Roles at High Growth AI Startups this week
Software Engineer - Data Infrastructure at Luma AI
Staff Software Engineer, Compute Services at CoreWeave
Senior Frontend Engineer at Typeface
Staff/Principal Software Engineer, Web Applications at Fireworks AI
Senior Software Engineer, iOS at Otter.ai
Software Engineer - Security at ClickHouse
Senior/Staff Software Engineer, Runtime at Plus
Senior Full Stack Engineer at Invisible AI
High Salary General SWE Roles this week
Principal Platform Software Engineer - OpenBMC Platform Architect at NVIDIA
Director of Engineering and Site Lead at Harvey
Managing Director, Software Engineering at West Monroe
Tech Lead Backend Software Engineer at TikTok
Senior Manager, AI ML Applied Field Engineering at Snowflake
Sr. Sales Engineer at Tenstorrent
Software Engineering PMTS at Salesforce
Software Engineer, Model Context Protocol at Anthropic
SPONSOR US
Get your product in front of more than 1,000,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing hi@bytebytego.com.