As we navigate through 2024, the cyber threat landscape continues to evolve, bringing new challenges for both businesses and individual consumers. The latest OpenText Threat Report provides insight into these changes, offering vital insights that help us prepare and protect ourselves against emerging threats. Here’s what you need to know:
The Resilience of Ransomware
Ransomware remains a formidable adversary, with groups like LockBit demonstrating an uncanny ability to bounce back even after significant law enforcement actions. Despite a recent crackdown that saw authorities dismantle its infrastructure, LockBit swiftly resumed operations, even taunting law enforcement agencies in the process. This adaptability highlights how resourceful ransomware groups have become, enabling them to evade detection and persistently challenge defenders.
For businesses, this means implementing a comprehensive incident response plan that includes secure, immutable backups and regular testing to ensure rapid recovery in the event of an attack. Consumers should also take measures like frequently backing up their data to an external drive or cloud solution. This resilience requires ongoing vigilance and robust security measures for everyone involved.
Malware Infections on the Rise
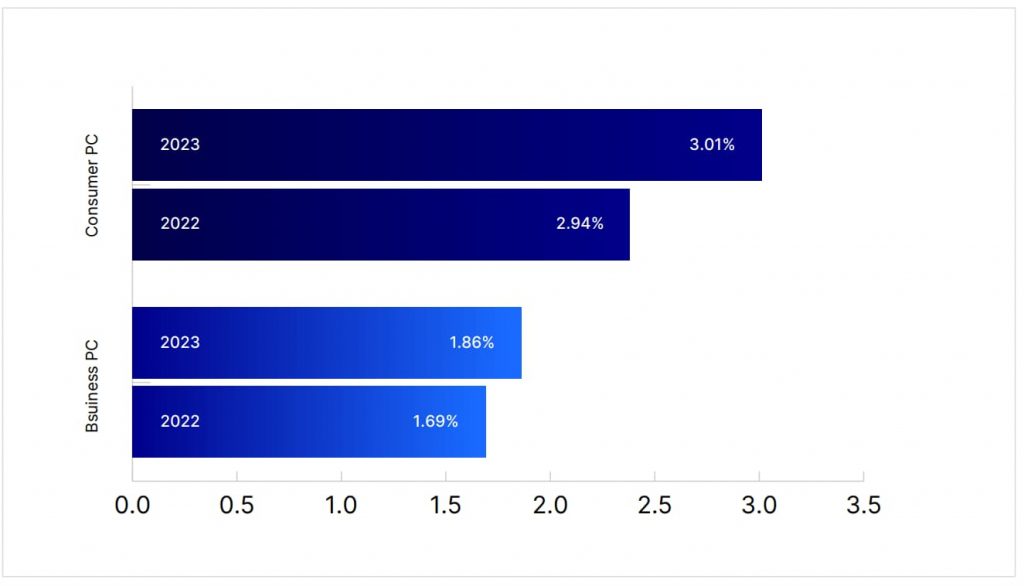
For the first time in years, malware infection rates are rising among both businesses and consumers. The uptick is primarily attributed to attackers leveraging advanced tools like generative artificial intelligence (AI), which helps them craft malware that’s more sophisticated and adaptive. Malware variants are becoming more difficult to detect, and infection methods are increasingly creative, such as using enticing email attachments or redirecting users to malicious sites via QR codes.
This new wave of malware infections serves as a stark reminder for businesses and individuals to strengthen their cyber defenses. Keep all devices updated with the latest security patches, and use reputable antivirus solutions that can block suspicious downloads and identify malicious software. Additionally, be wary of unexpected attachments or links and avoid clicking on anything that looks suspicious.
Phishing Gets Personal
Phishing attacks are becoming more sophisticated, thanks to tools like generative AI, which enable attackers to personalize their campaigns for maximum impact. What was once a clear distinction between mass phishing emails and more targeted spear-phishing attempts is now blurring, making it harder to distinguish between the two. Attackers can craft convincing emails that mimic legitimate brands, logos, and domains to trick unsuspecting victims into providing sensitive information or clicking malicious links.
For both businesses and consumers, this trend emphasizes the need for increased vigilance and cybersecurity awareness. Educate yourself on common phishing tactics and train employees to recognize fraudulent emails. Multi-factor authentication (MFA) can add a vital layer of protection, and carefully inspect email addresses and links before taking any action.
The Critical Role of Cyber Resilience
The report underscores the importance of adopting a multi-layered defense strategy to mitigate the impact of these evolving threats. Cyber resilience involves proactive measures to prevent attacks while also ensuring you can quickly recover if a breach occurs. For businesses, this means implementing strong antivirus software, endpoint protection solutions, and regular software updates. For consumers, being alert to suspicious emails, using secure passwords, and frequently backing up data is crucial.
A multi-layered approach integrates different layers of defense, making it much harder for an attacker to compromise all systems simultaneously. Combine antivirus tools with DNS protection, endpoint monitoring, and user training for comprehensive protection.
Regional Disparities in Cyber Threats
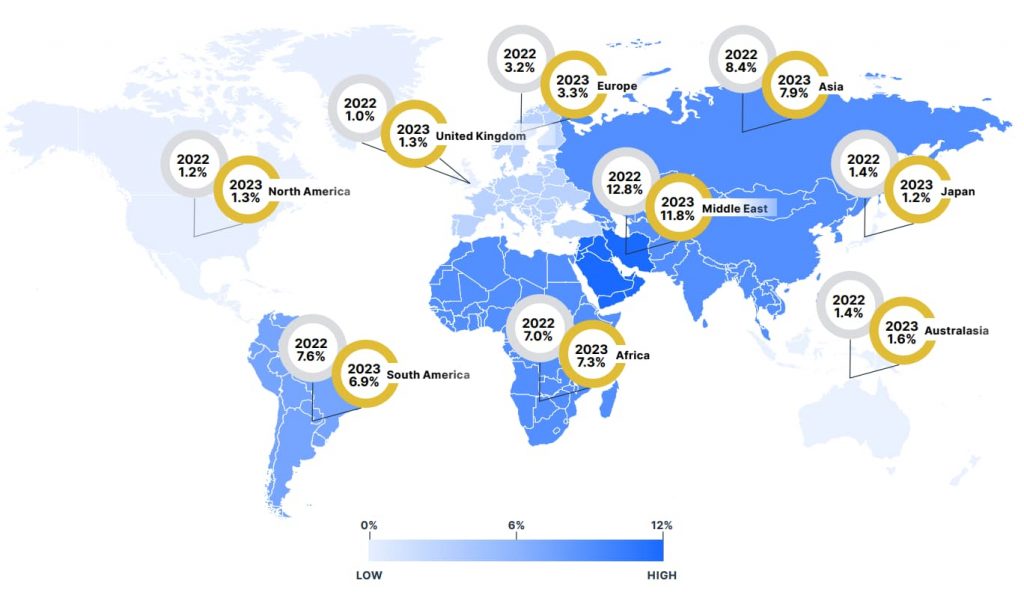
Geographical factors significantly influence the prevalence and nature of cyber threats. The report identifies regions like Asia, Africa, and South America facing higher infection rates than North America and Europe, partly due to differing economic conditions, cybersecurity maturity, and regulatory environments. Malware campaigns are often tailored to exploit regional nuances, such as the availability of local payment methods or common software vulnerabilities.
Businesses operating globally should adapt their cybersecurity strategies to account for these disparities, ensuring protections are tailored to local risks. Similarly, consumers should stay updated on the regional trends to better prepare for prevalent scams and threats in their area.
Industry-Specific Risks
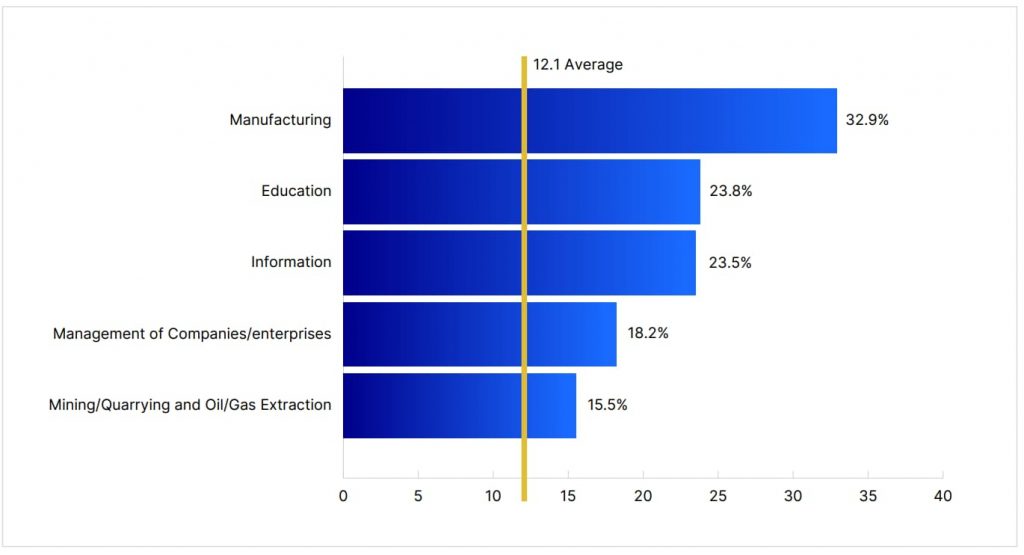
Specific industries like manufacturing, education, and healthcare are frequently targeted due to the valuable data they hold and the potential disruption caused by successful attacks. Manufacturing is particularly vulnerable to ransomware due to the high cost of production stoppages, which can prompt quicker ransom payments. Educational institutions, on the other hand, often have limited cybersecurity budgets, leaving them vulnerable to malware and phishing attacks that can compromise student and faculty data.
While businesses in these industries must enhance their cyber defenses and train staff accordingly, consumers should also be aware of how these attacks could indirectly impact them. For instance, a ransomware attack on a healthcare provider could lead to data breaches exposing patient information.
Recommendations for Enhancing Cybersecurity
- Implement Advanced Email Security: Use systems that can effectively block malicious attachments and links to protect against phishing.Stay Updated with Regular Patches: Keeping your software up-to-date is a critical step in protecting against vulnerabilities that could be exploited by attackers.Invest in Comprehensive Cybersecurity Training: Both businesses and individual users should engage in ongoing education on cybersecurity best practices to recognize and mitigate threats.Adopt Robust Backup Solutions: Ensure that all important data is backed up regularly and securely. This not only protects information but also minimizes disruption in the event of a cyber attack.
The 2024 OpenText Threat Perspective serves as a crucial resource, offering insights that are essential for both businesses and consumers aiming to navigate the complexities of today’s cyber threat landscape. By understanding these threats and implementing a multi-layered defense strategy, we can significantly enhance our collective cyber resilience.
The post Key Insights from the OpenText 2024 Threat Perspective appeared first on Webroot Blog.

