The Ultimate Weapon for Software Architect 🗺️ (Sponsored)
What if you could instantly identify the only 3 functionalities to test for non-regression after modifying a complex Java class?
What if you could visualize the ripple effect, from database to front-end, of changing a column data type?
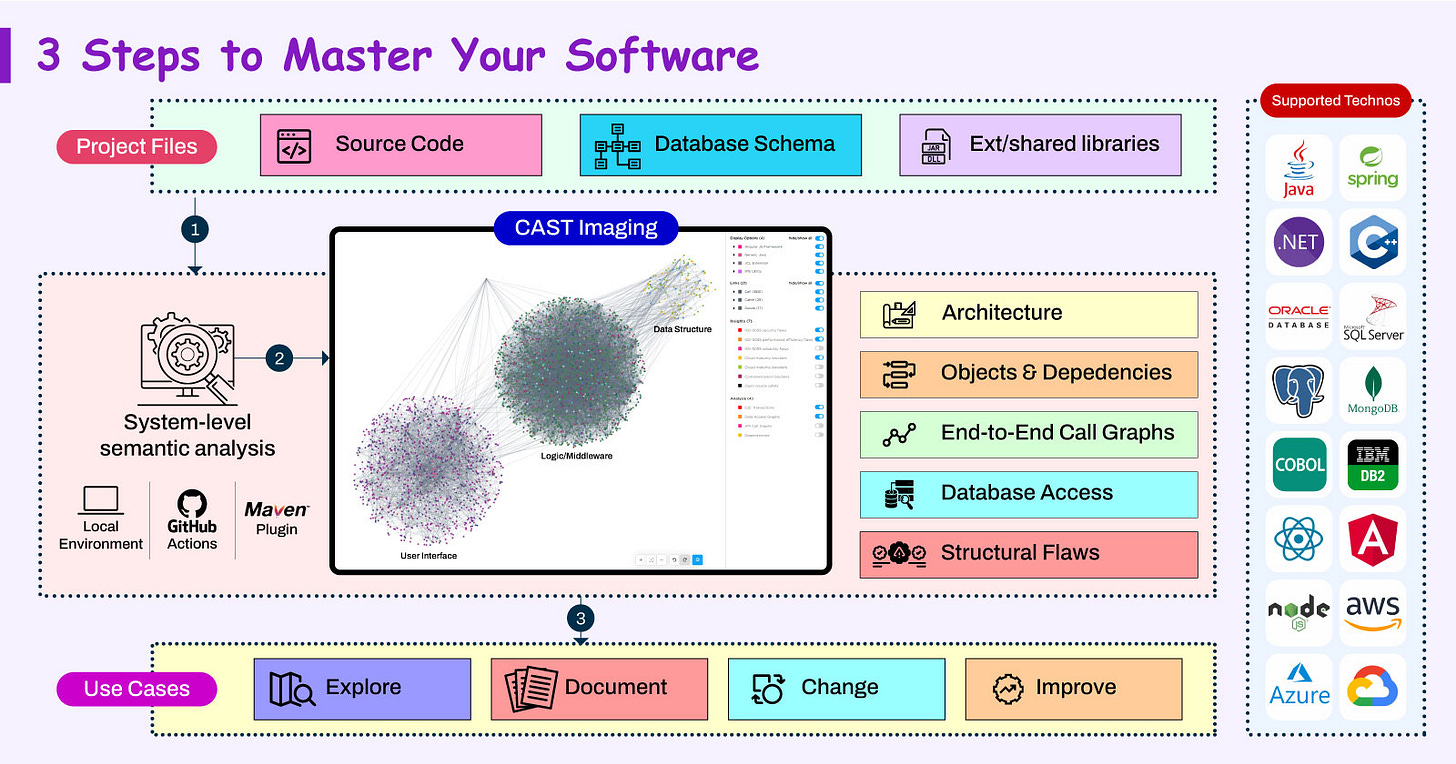
Master your application with the architects’ ultimate weapon🗺️
CAST Imaging automatically maps any application’s inner workings:
Visualize all dependencies, explore database access
Trace end-to-end data & call flows, assess change impact
Identify structural flaws typically missed by code quality tools
Stop wasting countless hours reverse-engineering your code manually.
Move faster with CAST Imaging, the automated software mapping tech.
CAST Imaging supports any mix of Java/JEE, .NET, C#, COBOL, SQL, and 100+ other languages, frameworks, and database engines.
This week’s system design refresher:
Software Architect Knowledge Map
What is Retrieval-Augmented Generation (RAG)?
How Amazon S3 Works?
How Two-factor Authentication (2FA) Works?
SPONSOR US
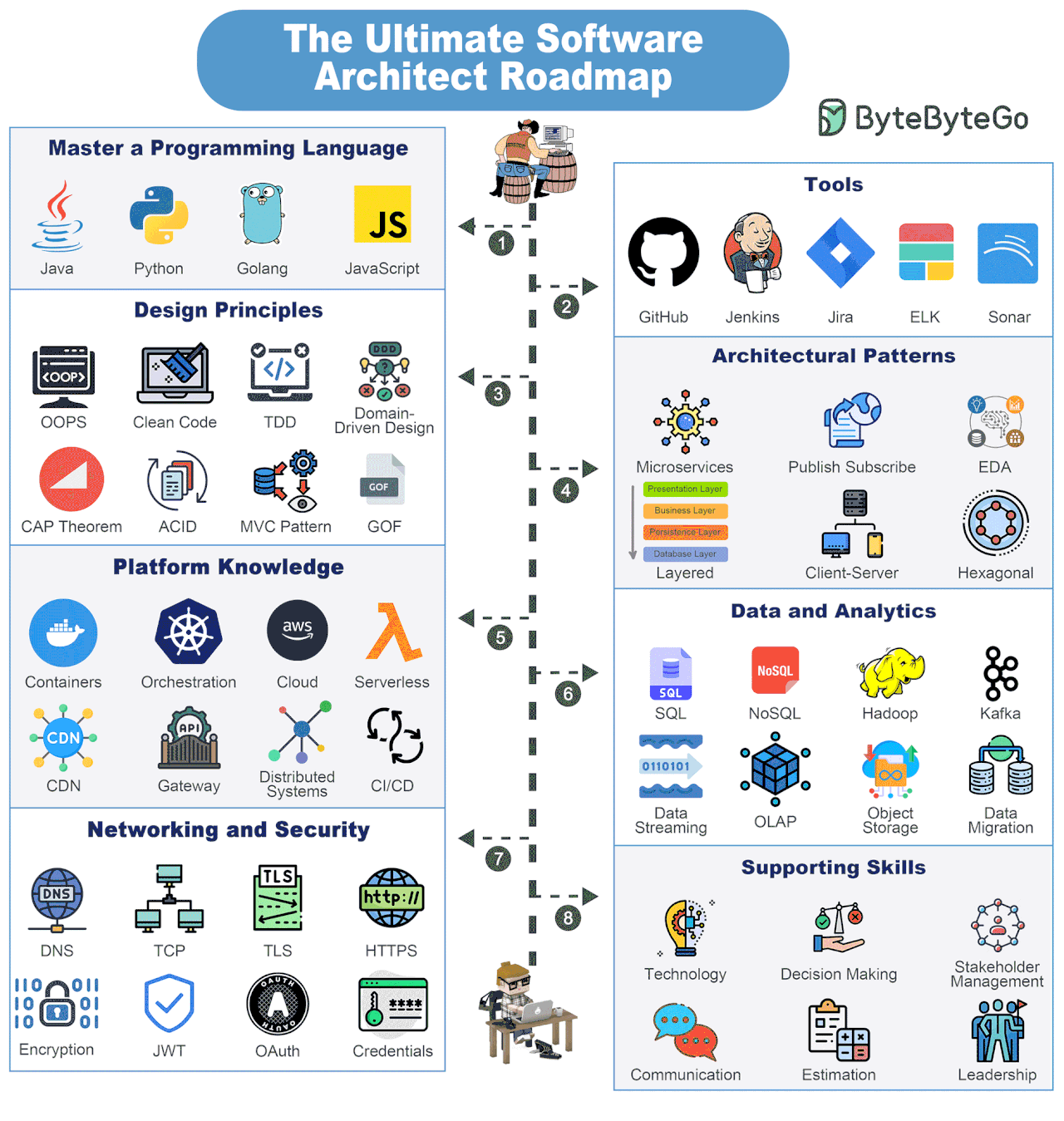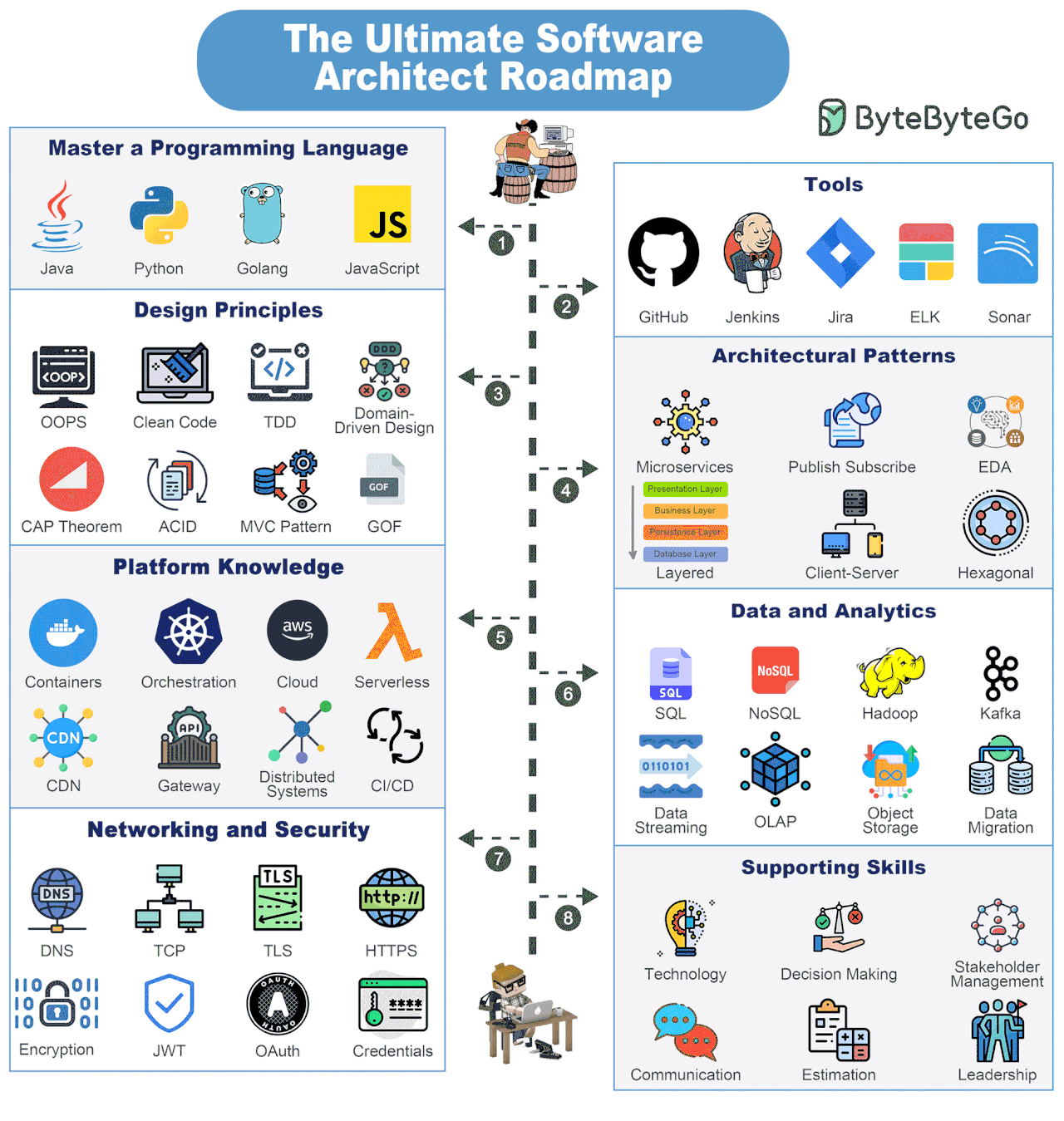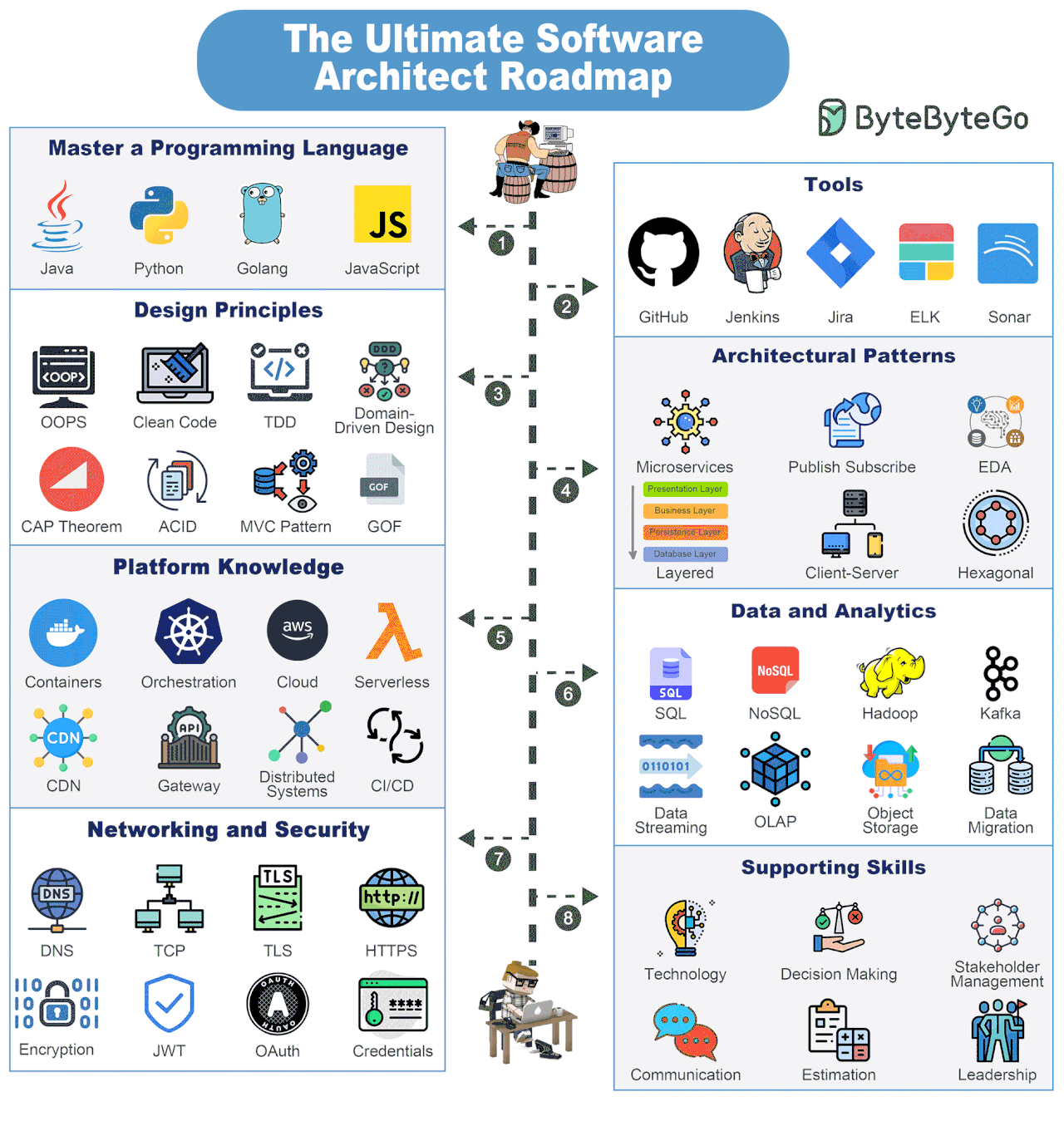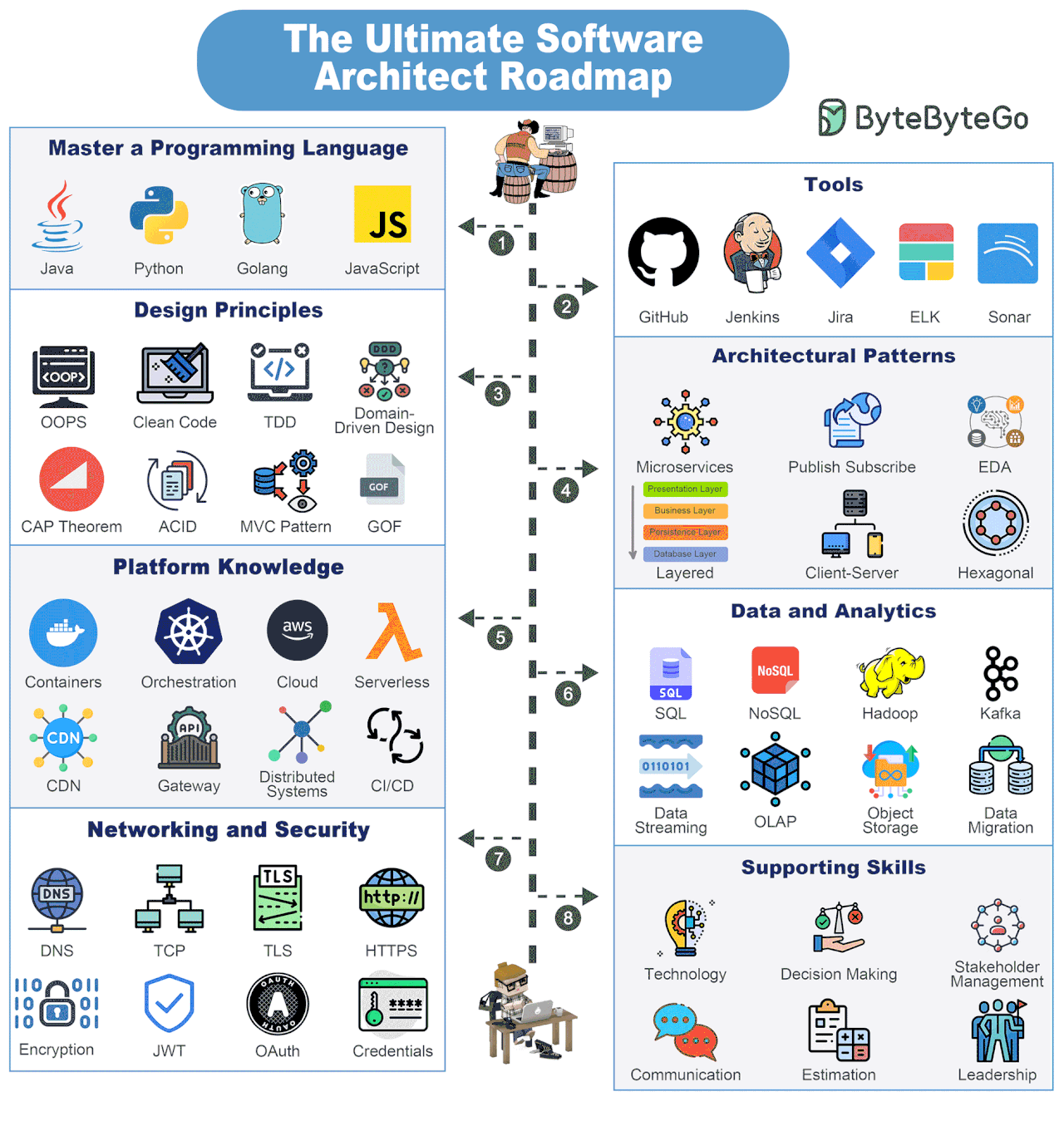
Software Architect Knowledge Map
Becoming a Software Architect is a journey where you are always learning. But there are some things you must definitely strive to know.
Master a Programming Language
Look to master 1-2 programming languages such as Java, Python, Golang, JavaScript, etc.
Tools
Build proficiency with key tools such as GitHub, Jenkins, Jira, ELK, Sonar, etc.
Design Principles
Learn about important design principles such as OOPS, Clean Code, TDD, DDD, CAP Theorem, MVC Pattern, ACID, and GOF.
Architectural Principles
Become proficient in multiple architectural patterns such as Microservices, Publish-Subscribe, Layered, Event-Driven, Client-Server, Hexagonal, etc.
Platform Knowledge
Get to know about several platforms such as containers, orchestration, cloud, serverless, CDN, API Gateways, Distributed Systems, and CI/CD
Data Analytics
Build a solid knowledge of data and analytics components like SQL and NoSQL databases, data streaming solutions with Kafka, object storage, data migration, OLAP, and so on.
Networking and Security
Learn about networking and security concepts such as DNS, TCP, TLS, HTTPS, Encryption, JWT, OAuth, and Credential Management.
Supporting Skills
Apart from technical, software architects also need several supporting skills such as decision-making, technology knowledge, stakeholder management, communication, estimation, leadership, etc.
Over to you - What else would you add to the roadmap?
Free Roadmap: Future-proof your Dev Skills (Sponsored)
Feeling the pressure to master DevOps while juggling your development responsibilities?
You're not alone.
That’s why we've created an actionable DevOps Roadmap specifically for software engineers looking to level up their operational skills without getting overwhelmed.
This clear, step-by-step guide maps out the essential DevOps tools, practices, and concepts that directly enhance a developer's career trajectory.
From containerization to CI/CD pipelines, from cloud to monitoring solutions – we've distilled years of DevOps expertise into an actionable learning path.
Join thousands of developers who've transformed their technical capabilities with our structured approach:
This guide was created exclusively for ByteByteGo readers by TechWorld with Nana | 1M+ ENGINEERS TRAINED
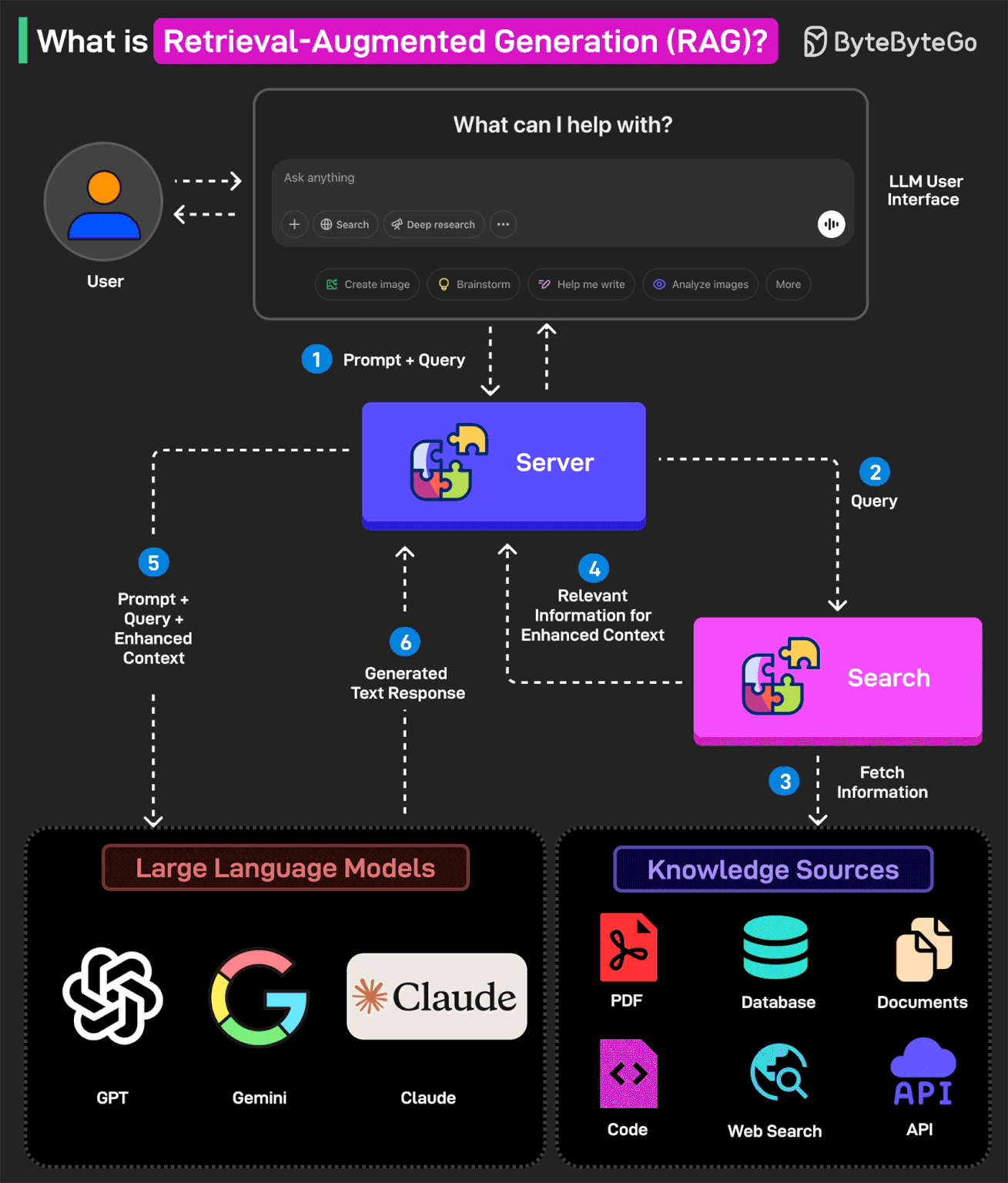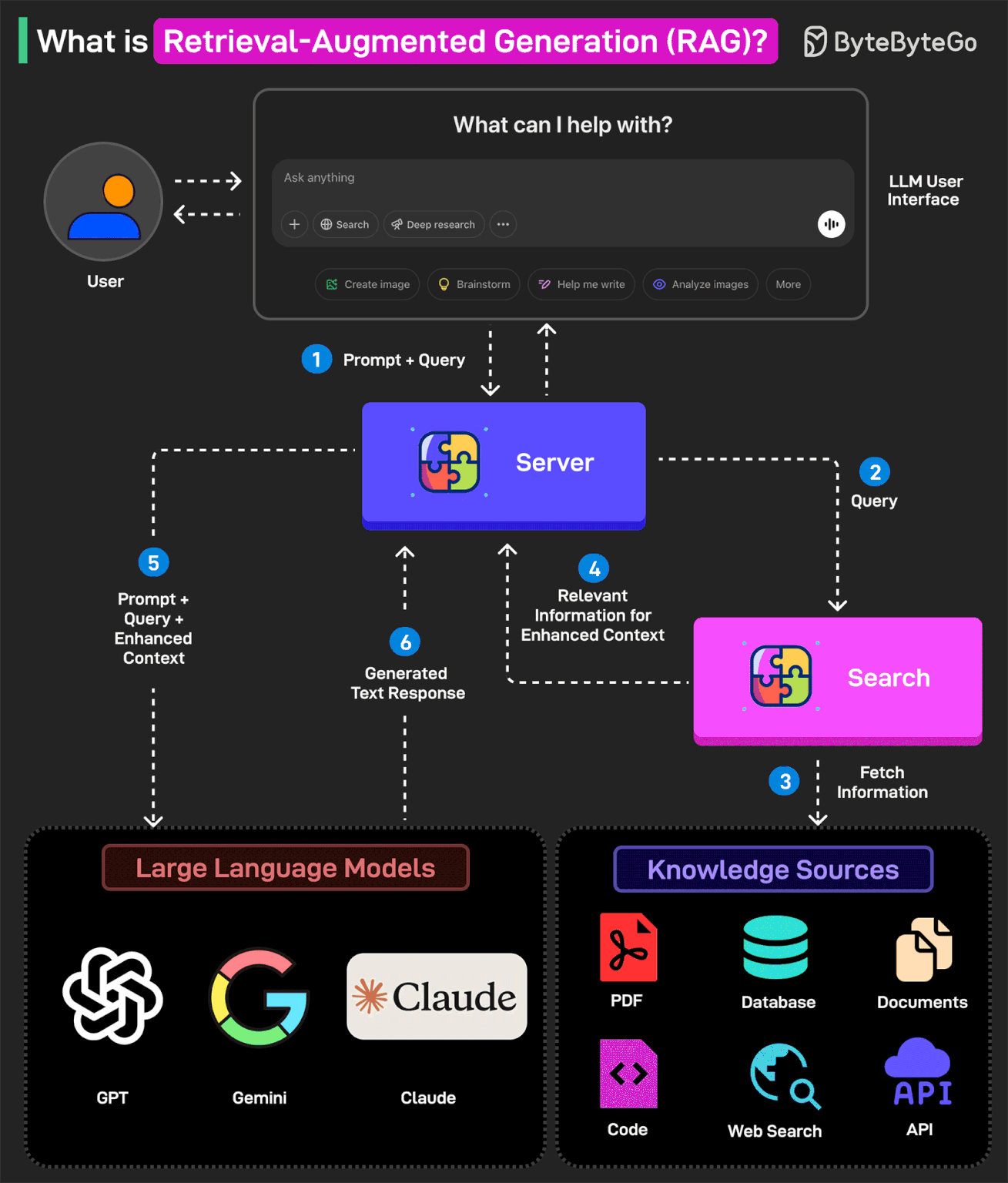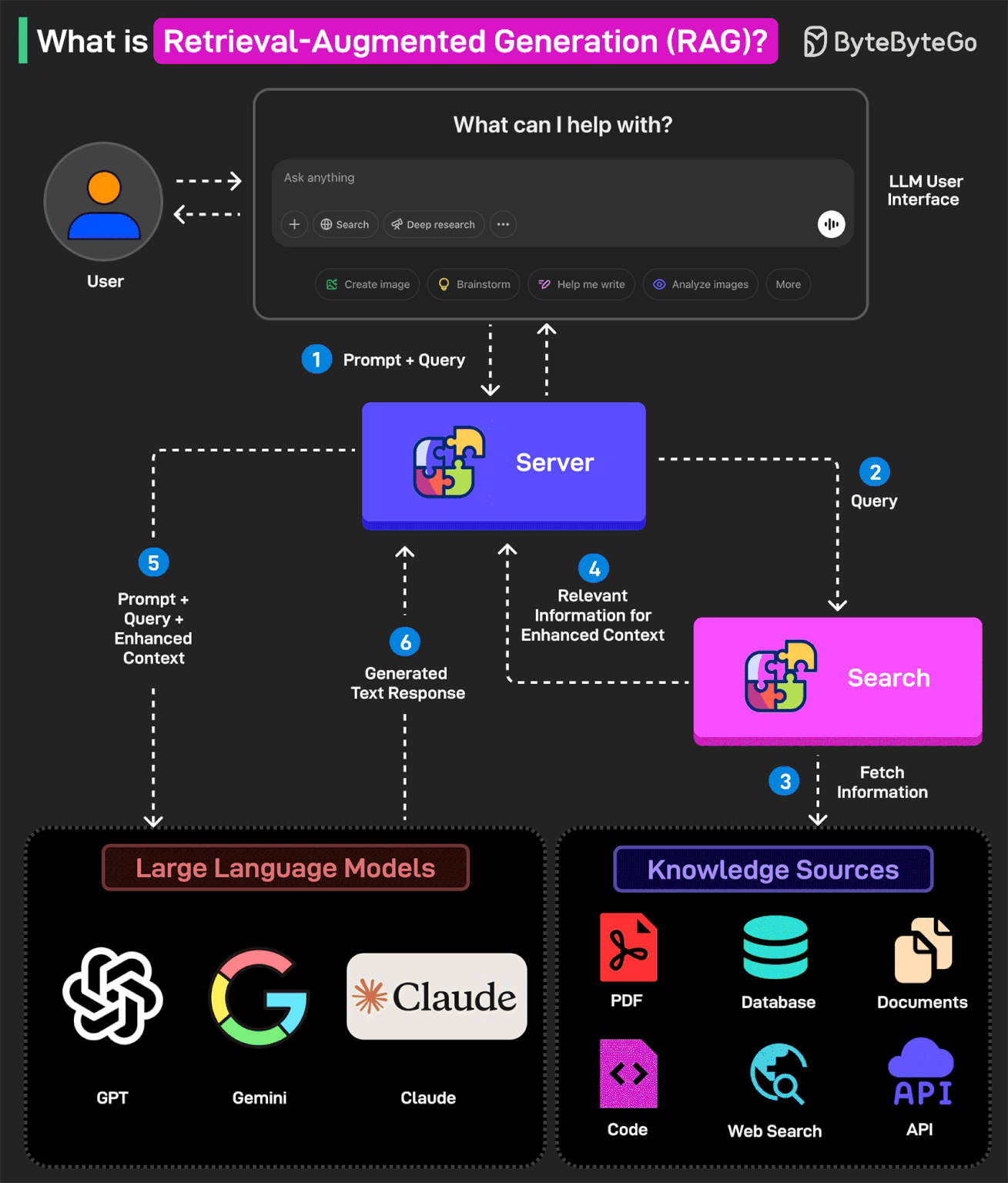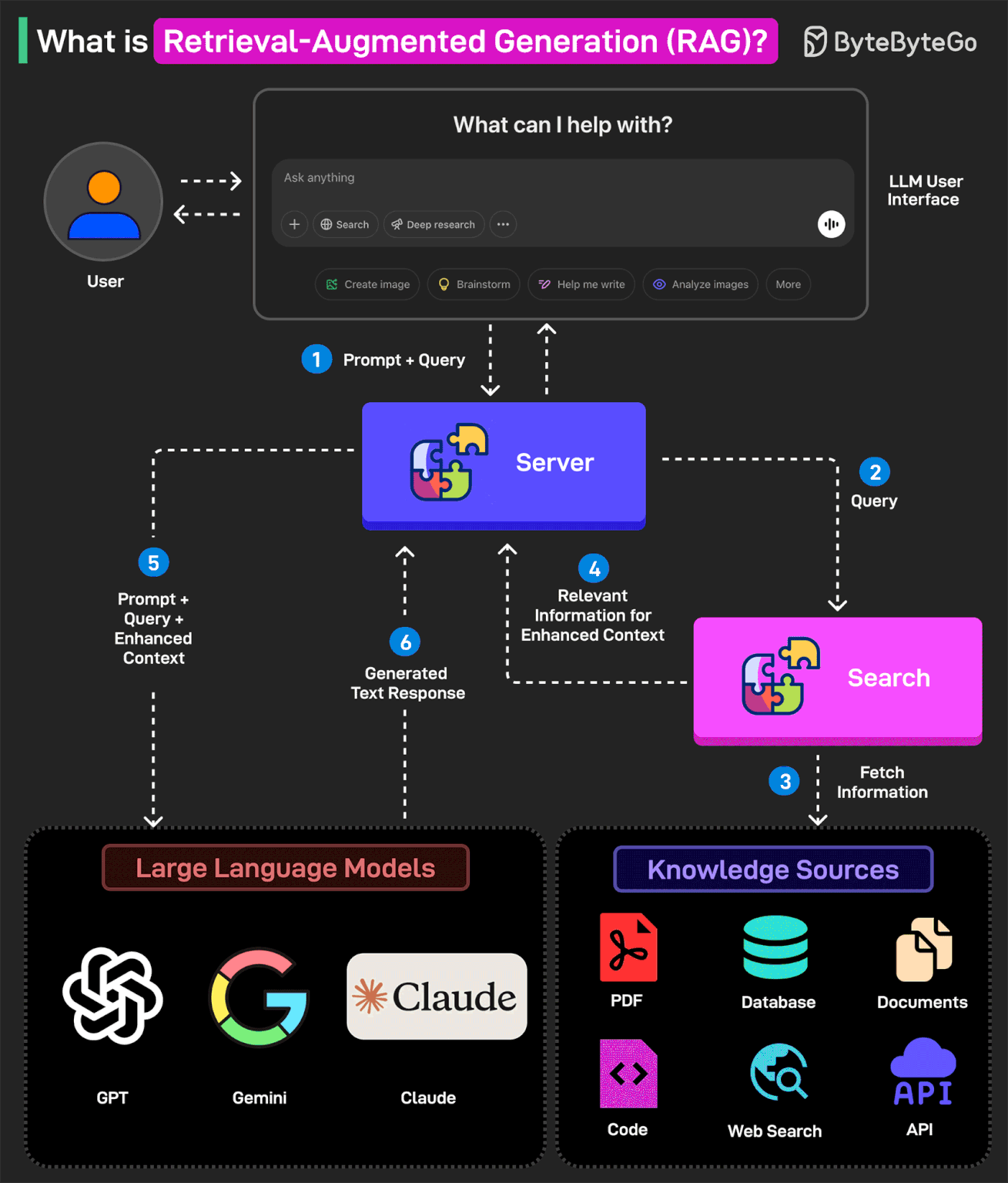
What is Retrieval-Augmented Generation (RAG)?
RAG is the process of optimizing an LLM's output to reference a specific knowledge base that may not have been part of its training data before generating a response.
In other words, RAG helps extend the powerful capabilities of LLMs to specific domains or knowledge bases without the need for additional training.
Here’s how RAG works:
1 - The user writes a query prompt in the LLM’s user interface. This query is passed to the backend server where it is converted to a vector representation.
2 - The query is sent to a search system.
3 - This search system can refer to various knowledge sources such as PDFs, Web Search, Code-bases, Documents, Database, or APIs to fetch relevant information to answer the query.
4 - The fetched information is sent back to the RAG model.
5 - The model augments the original user input by adding the fetched information to the context and sending it to the LLM endpoint. Various LLM options are Open AI’s GPT, Claude Sonnet, Google Gemini, and so on.
6 - The LLM generates an answer based on the enhanced context and provides a response to the user.
Over to you: Have you used RAG with your favorite LLM?
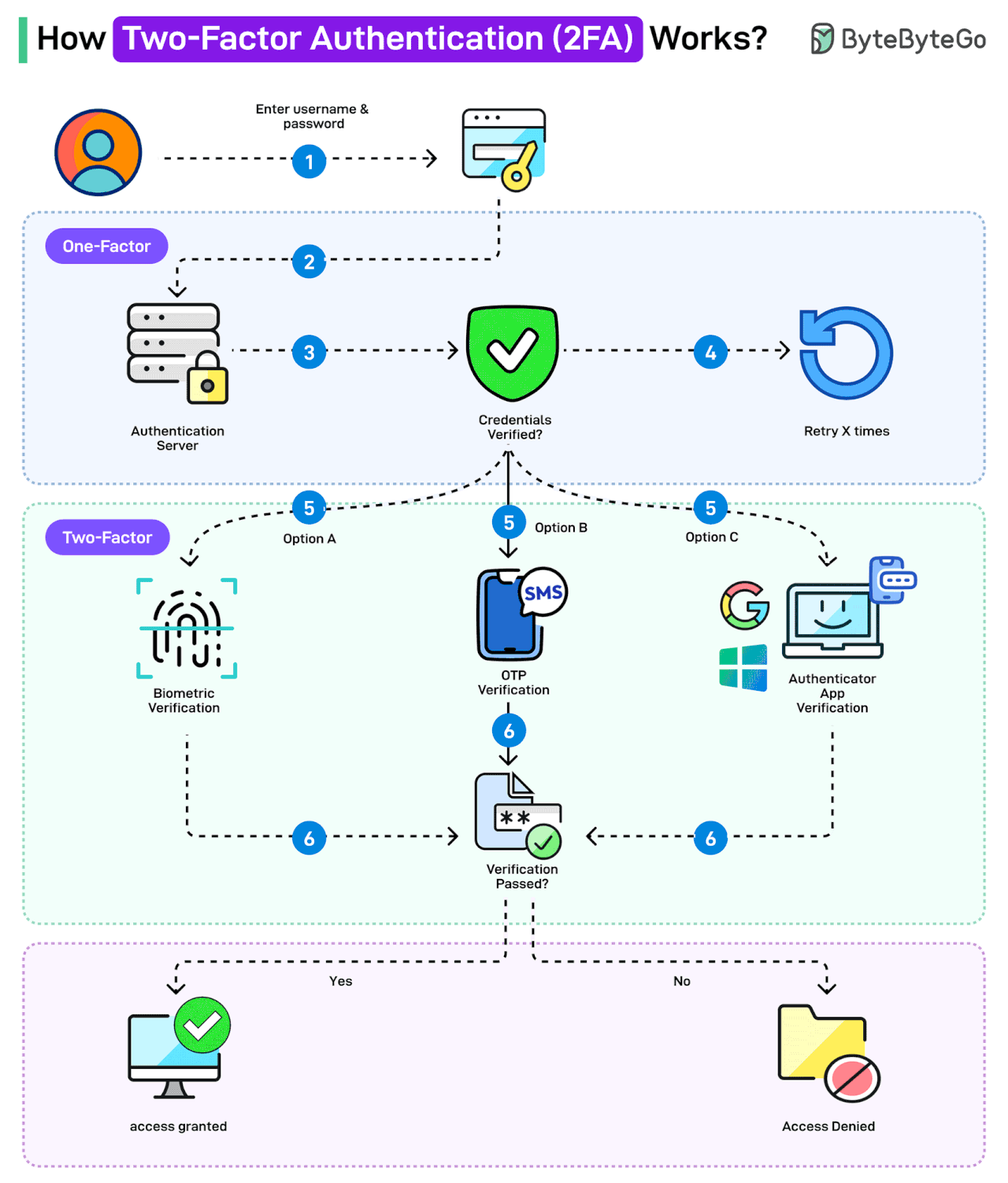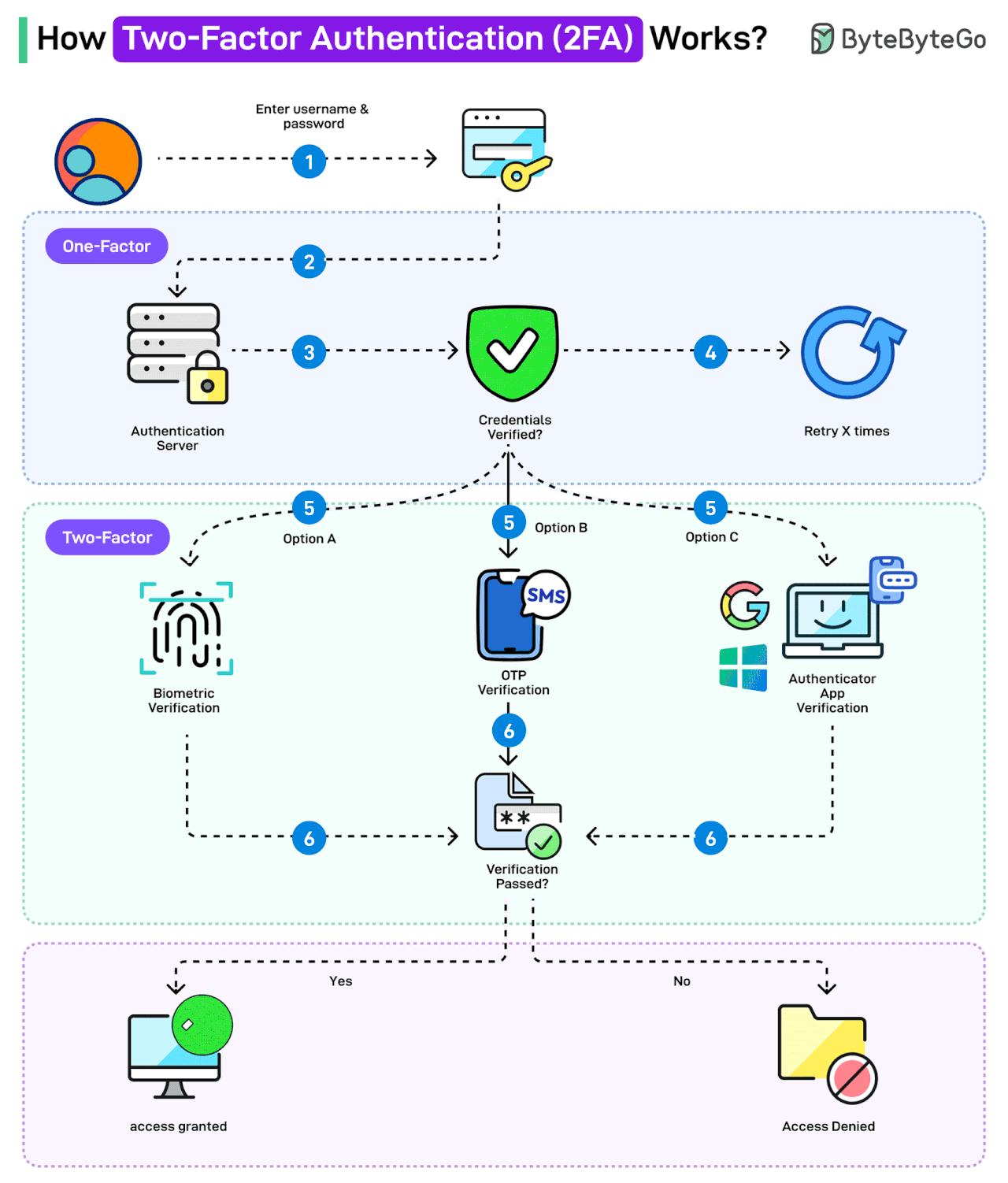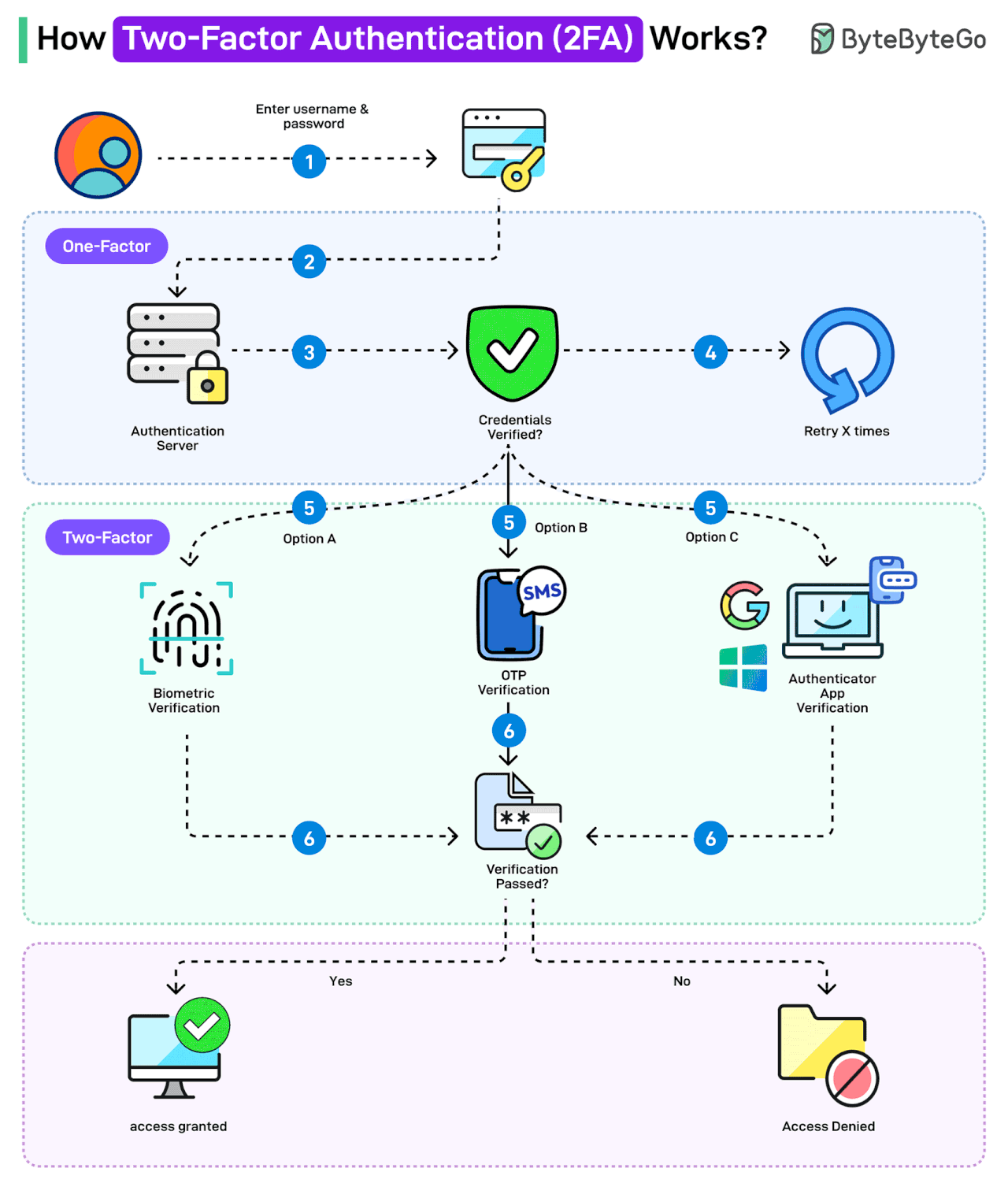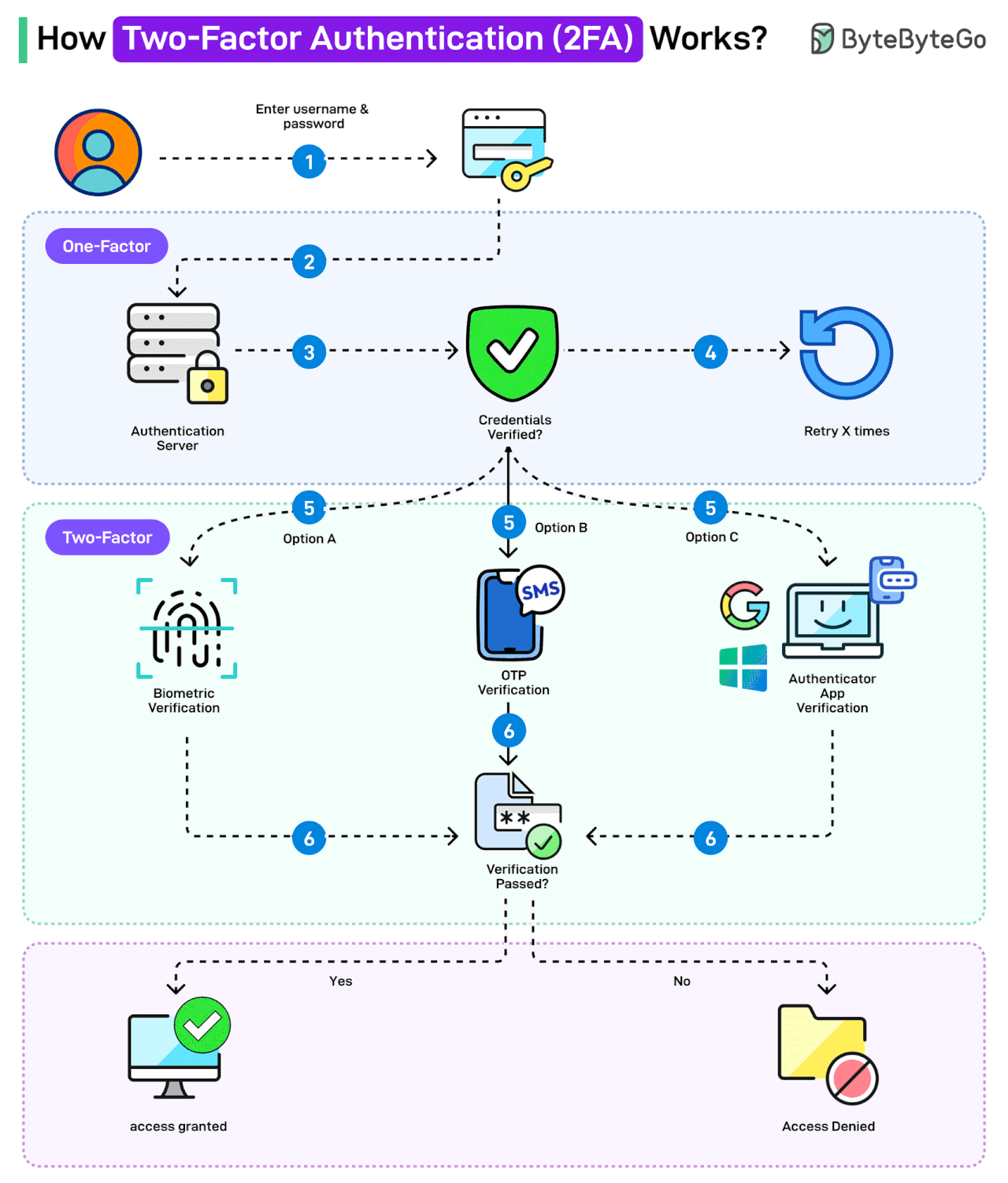
How Two-factor Authentication (2FA) Works?
Two-factor authentication (2FA) is a type of multi-factor authentication that makes accounts more secure.
The idea behind 2FA is that you need to provide two identifying factors to prove your identity and gain access to your account.
The first factor is the knowledge factor, where a user needs to know a secret, such as a password. The second factor depends on the possession factor (such as RSA, authenticator app) or inherence factor (biometrics).
Here’s how 2FA works:
The user enters username and password. This is for the first level of authentication, also known as single-factor.
The authentication request goes to the authentication server.
The authentication credentials are verified.
In case of any incorrect credentials, a certain number of retries may be allowed.
If the credentials are correct, the two-factor authentication kicks in. There are multiple options available: biometric verification, OTP verification, or Authenticator App Verification. Organizations like Google and Microsoft also provide such apps.
The user verifies using the chosen option.
If the verification fails, access is denied. However, if verification succeeds, access is granted.
Note that the OTP verification using SMS is often considered less secure as a 2FA mechanism.
Over to you - Have you used two-factor authentication?
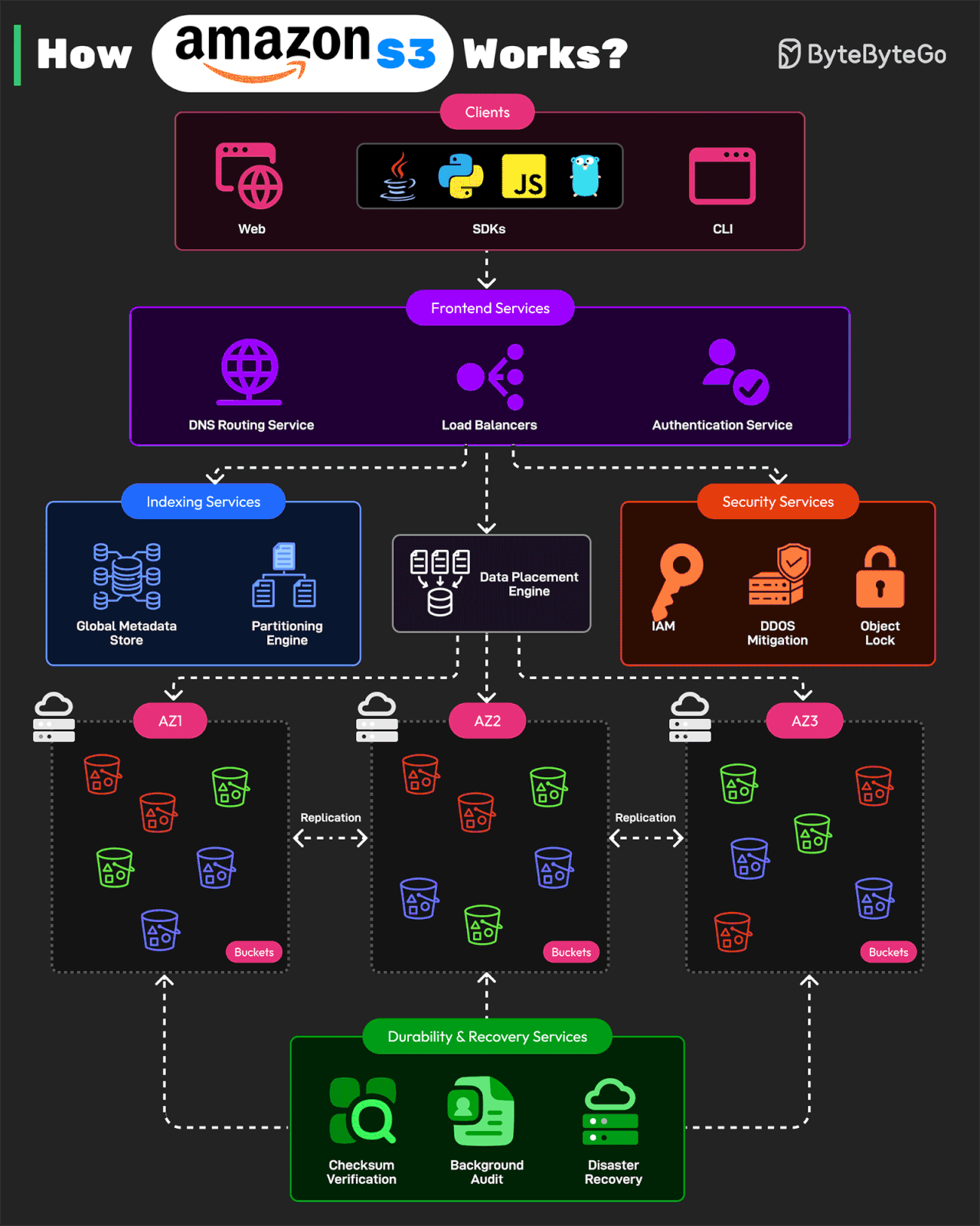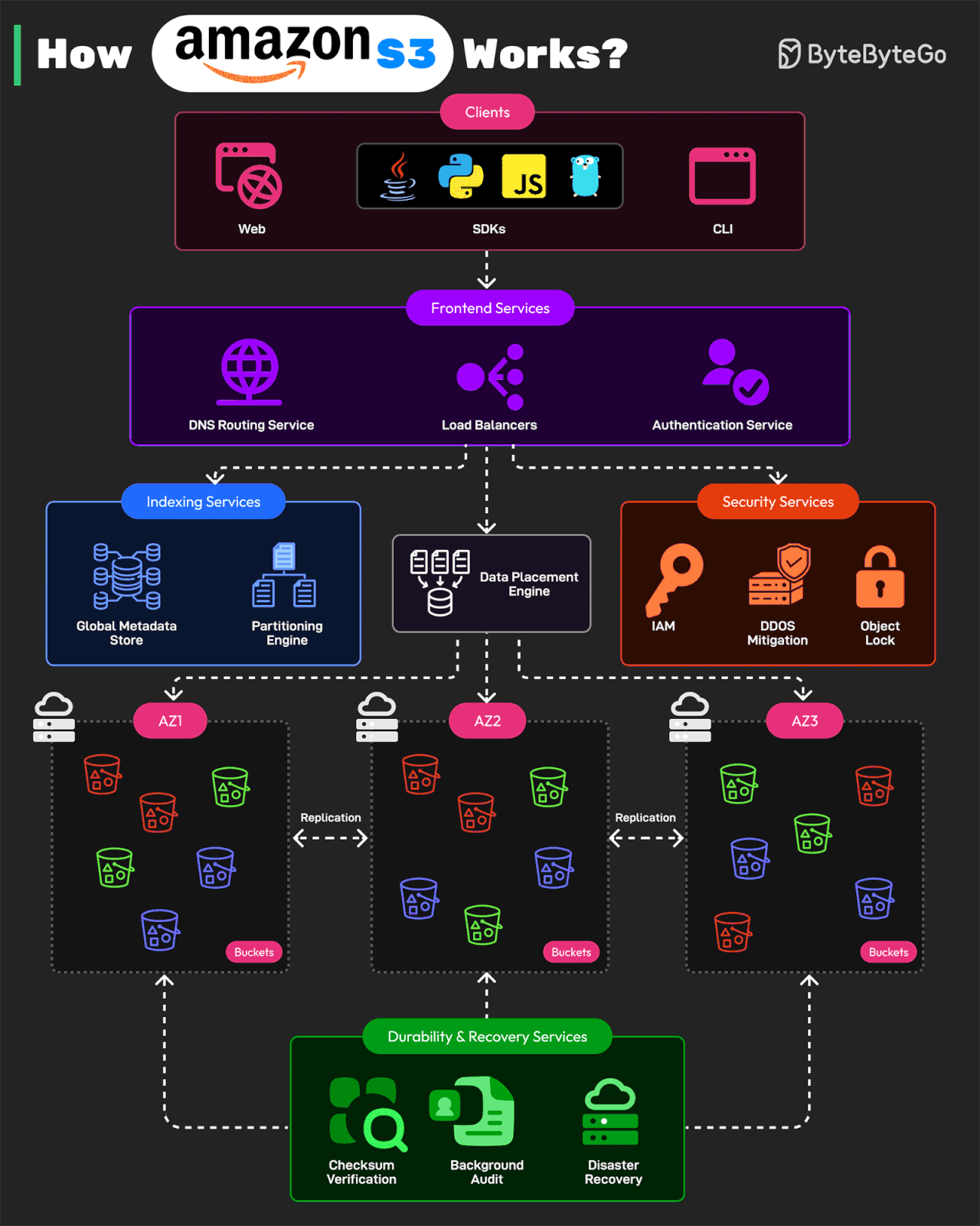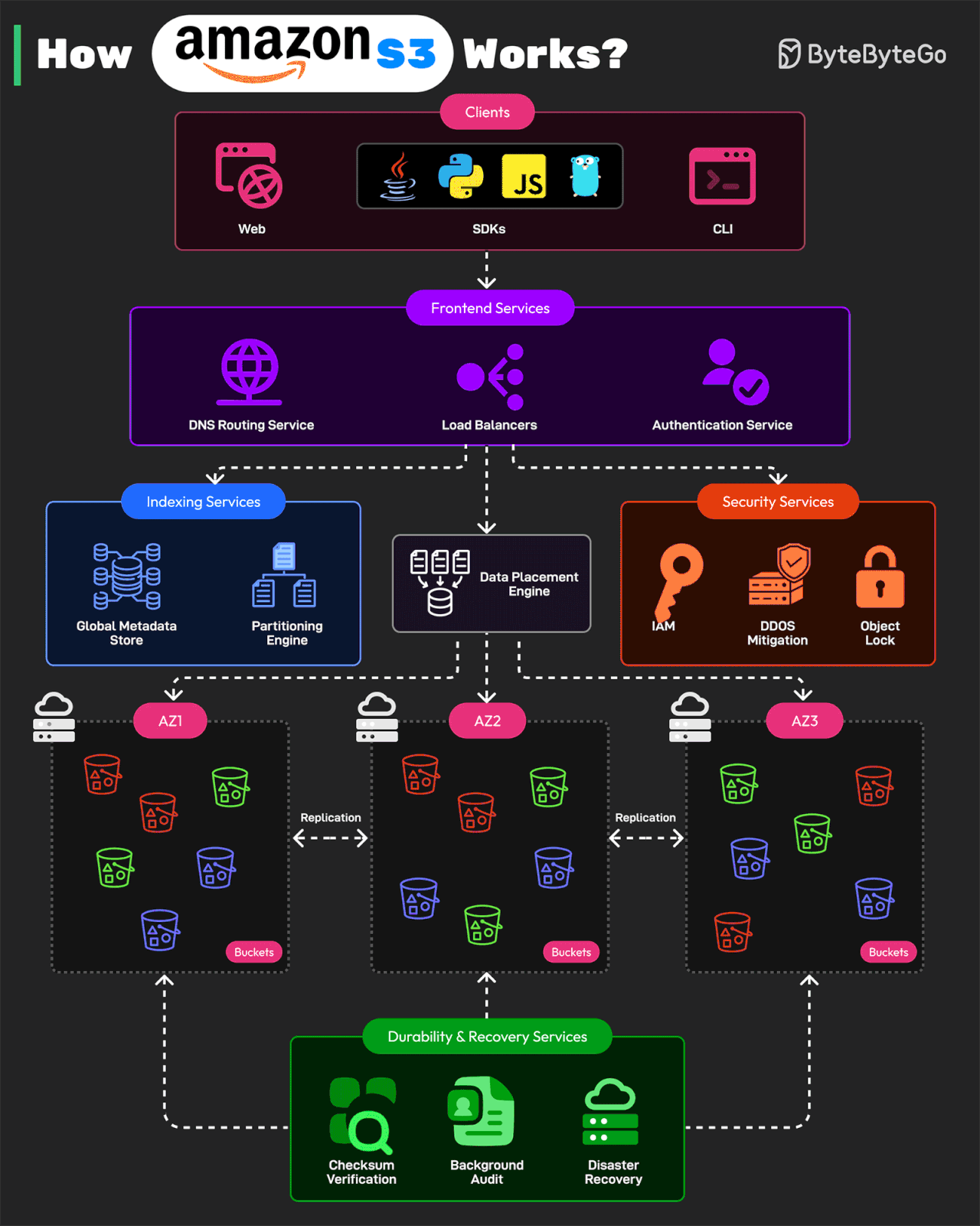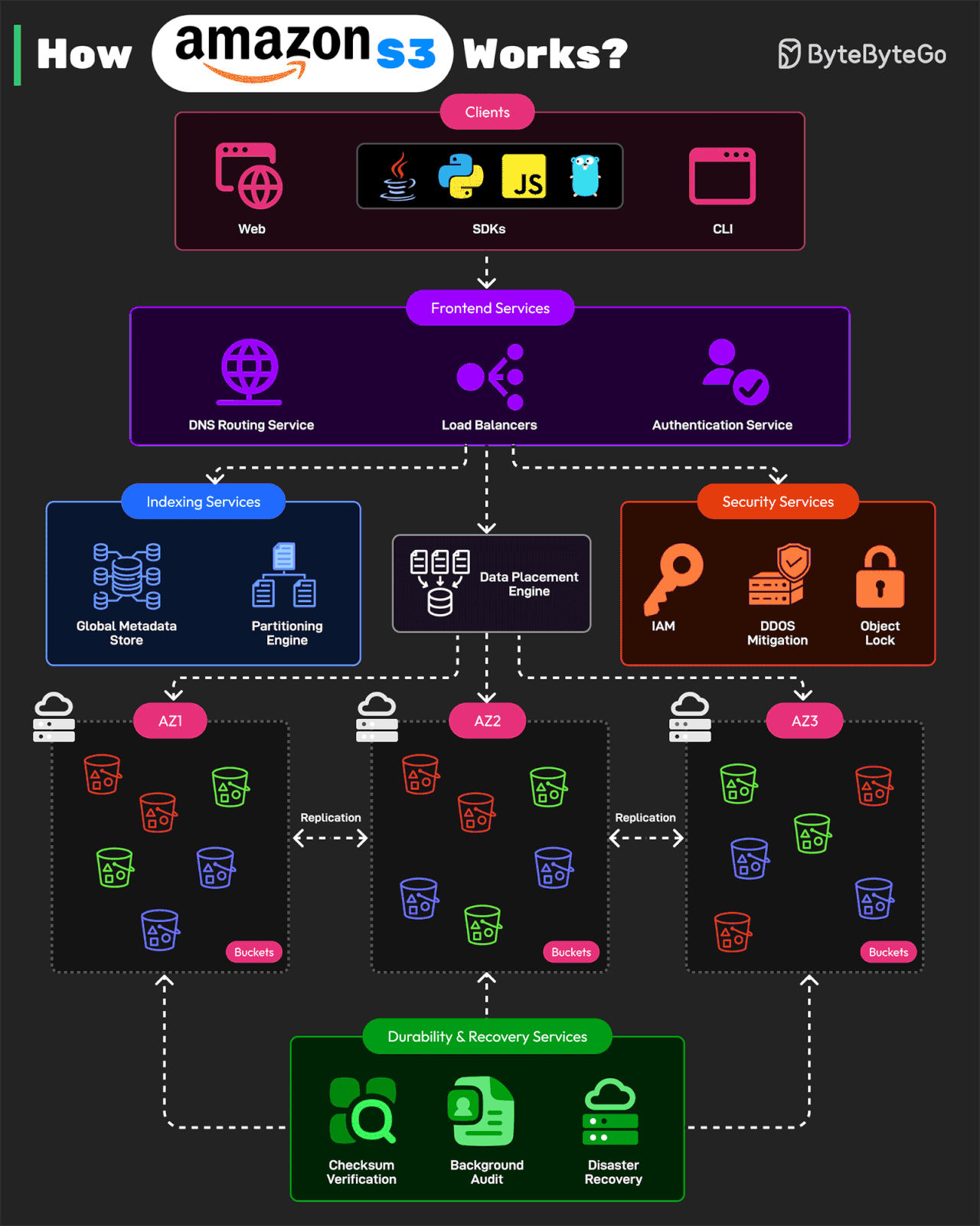
How Amazon S3 Works?
This post is based on:
AWS re:Invent 2023 - Dive deep on Amazon S3 video
Building and operating a pretty big storage system called S3 published on All Things Distributed.
Amazon S3 is one of the largest and most complex distributed storage systems in the world. It processes millions of requests per second and stores over 350 trillion objects while maintaining 99.999999999% durability.
AWS architected S3 using a microservices-based design
Here’s how it works:
Front-end Request Handling Services
These services receive API requests from clients. The clients can be web, CLI, and SDKs for programming languages like Java, Python, JS, or Golang. After receiving the request, the services authenticate users, validate requests, and route them to the correct storage service. The services consist of DNS routing, authentication service, and load balancing.
Indexing and Metadata Services
Every object stored in S3 is assigned a unique identifier and metadata. The indexing services track object locations. They consist of a global metadata store and partitioning engine.
Storage and Data Placement Services
This part handles the physical storage of objects across multiple S3 nodes. To protect against data loss, it uses erasure coding and multi-AZ replication.
Durability and Recovery Services
These services ensure data integrity and fault recovery. They consist of checksum verification, background auditing, and disaster recovery.
Security and Compliance Services
These services protect S3 from unauthorized access and support features such as IAM and bucket Policy, DDoS Mitigation, and Object Lockiand versioning.
Over to you: Have you used Amazon S3?
SPONSOR US
Get your product in front of more than 1,000,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing sponsorship@bytebytego.com.