Since we last spoke about Tailscale, my post waslinked by Tailscale themselves, and I’m pleased to report Tailscalehas sponsored one of my podcasts a couple times.
With that in mind, I want to make it clear that they do not know I’m writingthis post, and have not requested anything of me with regard to my website.
I just cleanly solved a weird problem that’s been nagging me for a very longtime, and thanks to Tailscale, I was able to do so quite easily. I thoughtit was a great case study in what makes Tailscale so amazing.
The Issue
My parents have a network attached storage that they use for, among otherthings, recording security cameras locally. As such, they will occasionallyaccess it remotely, and thus having a SSL certificate is pretty much requiredthese days.
Thankfully, Synology makes it easy to request a Let’s Encrypt certificate.However, to do so requires you to have the router forward ports 80 and 443 tothe Synology. Generally speaking, I do not want those ports forwardedanywhere, so I only turn on those forwards when renewal time comes around.
Messing about with their in-home router is not easily accomplished from my house,45 minutes away from theirs. Furthermore, Let’s Encrypt certificates have to berefreshed every 90 days, so this dance happens quarterly.
The Complication
My predicament is complicated by my parents’ oddball ISP-issued routerrefusing to respond to network requests coming from outside the network. Evenover a traditional VPN hosted in their house, the router would not respond torequests from my house. This very well could have been user error, but that waswhat I experienced.
I needed a way to have packets from my computer appear to be originating onmy parents’ network.
Solution #1
My first solution to this was to host a docker container that basically exposedFirefox via the web. Yo dogg, I heard you like web browsers in your webbrowsers. So, the process was:
- Get on the VPN hosted at my folks’Get on the Firefox docker image via
http://192.168.1.xMake the port forwarding changes to their routerRequest a certificate renewal on their SynologyUndo the port forwarding changesThis worked just fine, but it was… involved.
Enter Tailscale
Tailscale is many many different features, all rolled into one product. A coretenet of Tailscale is that you should be able to migrate to Tailscale incrementally;you shouldn’t have to go all-in from the get-go. Tailscale has some features thathelp facilitate incremental adoption.
One of these features is Subnet routers; they are summarized quite well inthe Tailscale documentation:
In cases [where you can’t install Tailscale on every device], you can set upa subnet router to access these devices from your Tailscale network (knownas a tailnet). Subnet routers act as a gateway, relaying traffic from yourtailnet to a physical subnet.
In short, if you have a subnet router, you can route
local network → tailnet → subnet router → remote network
So, in principle, I could enter my parents’ router’s IP address into my browser,and it will load.
A New Complication
The way subnet routers typically work is that they effectively bridge two networkstogether. My parents’ network is 192.168.1.x; mine is 192.168.17.x. On thesurface, this seems fine, but so many networks are 192.168.1.x. I suspectthere will come a time one of my portable devices is on a 192.168.1.x network,and I may want to reach local devices on that network. By default, a basicsubnet router will intercept all requests to 192.168.1.x and try to serve themvia my parents’ network. That could easily make things wonky, and lead tomy devices not being able to reach local peers.
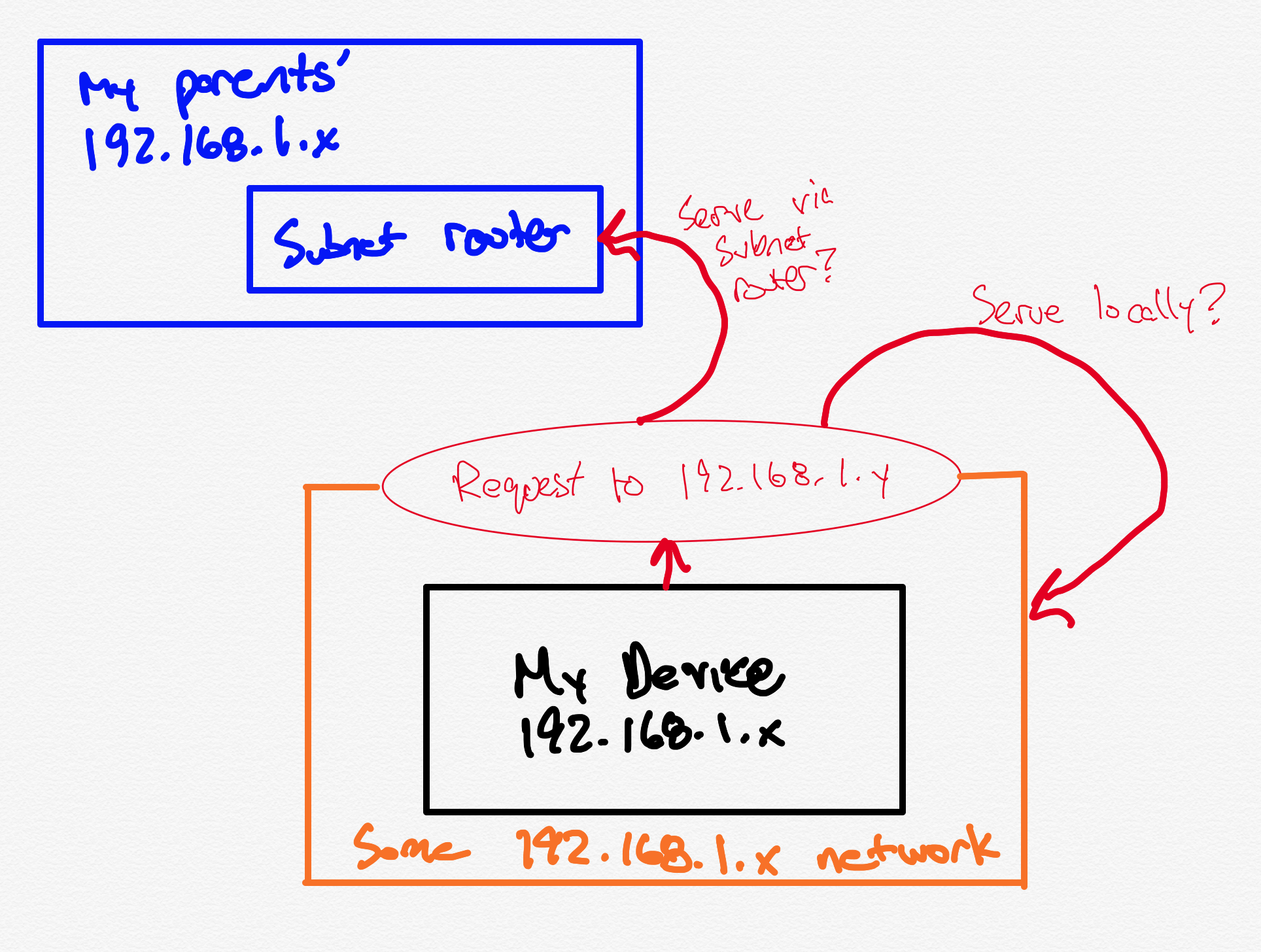
I’d like my parents’ network to stay… at my parents’ house. I’d just like to beable to peek into it for the purposes of tweaking their router’s settings everynow and again.
A New Solution
Tailscale has another trick up its sleeve that I realized would be a perfect fitfor this scenario. Tailscale offers “4via6” subnet routers. It occurredto me recently that this is the fix I’ve been looking for.
Tailscale’s problem statement is this:
In a large network, you may have existing subnets with overlapping IPv4 addresses.If there are two entirely separate virtual private clouds (VPCs) using the identicalset of IPs […]
That’s the scenario I’m worried about: I’m on a 192.168.1.x network, but myparents have already “claimed” the 192.168.1.x address space.
4via6 routers solve this by:
The 4via6 (“4 via 6”) subnet router feature provides an unambiguous,unique IPv6 address for each overlapping subnet, so a Tailscale node’straffic is routed to the correct device.
In short, I told the subnet router at my parents’ “I’d like you to expose this[otherwise internal] network on the tailnet only as IPv6”. That means all theIPv4 addresses in my parents’ house are exposed using a special IPv6 address:
fd7a:115c:a1e0:b1a:0:XXXX:YYYY:YYYY
Where:
fd7a:115c:a1e0:b1a:0 = a special Tailscale prefix to indicate 4via6XXXX = the identifier for the target subnetYYYY = the IPv4 address represented in hexSo, if I’ve designated my parents’ house as 123 (which is 7b in hex), then192.168.1.1 would be:
fd7a:115c:a1e0:b1a:0:7b:c0a8:101
Progress! However, an IPv6 address is not particularly memorable, which kinda stinks.
MagicDNS
Tailscale also offers “MagicDNS”, which does many things, but it willalso convert/resolve specially formed hostnames into the appropriate IPv6addresses.
So, if my tailnet name is smiley-tiger.ts.net, then I can open my parents’router’s configuration page by entering this URL into a browser on my computer:
http://192-168-1-1-via-123.smiley-tiger.ts.net/
That will automatically get resolved by MagicDNS to
http://fd7a:115c:a1e0:b1a:0:7b:c0a8:101
…which in turn lets me log into my parents’ router remotely, anytime, withoutany fiddling nor Docker containers required.
I can do this no matter what network my computer is on, as long as my subnetrouter at my parents’ is also on. Tailscale connects everything together.
It’s ✨ Magic ✨
This is what makes Tailscale so great — once you can connect your devicestogether, it opens a world of possibilities. Those possibilities easily extendto the devices on your tailnet, but they can extend to devices beyond yourtailnet, with just a little bit of work.
Seriously, Tailscale is so great; you really should try it.
At some point, I should probably look into automating some (all?) of thiscertificate renewal process, but for right now, I’m happy to bask in thework being far quicker and easier than it’s ever been before.

